
Over the last few years, the threat of ransomware attacks has made headlines not only for security practitioners, but also across the mainstream media. In 2017, the world was shaken by the now-infamous “WannaCry” and “Not Petya” attacks. However, this was not the beginning of this type of attack, it was simply the first time that ransomware captured the attention of the whole world. Since then, ransomware attacks have grown more widespread. This is partially due to a high yield potential, with some attacks yielding hundreds of thousands or millions of dollars in payouts, which are steadily increasing as well. Ransomware attacks can target any entity, from an individual all the way up to government bodies.
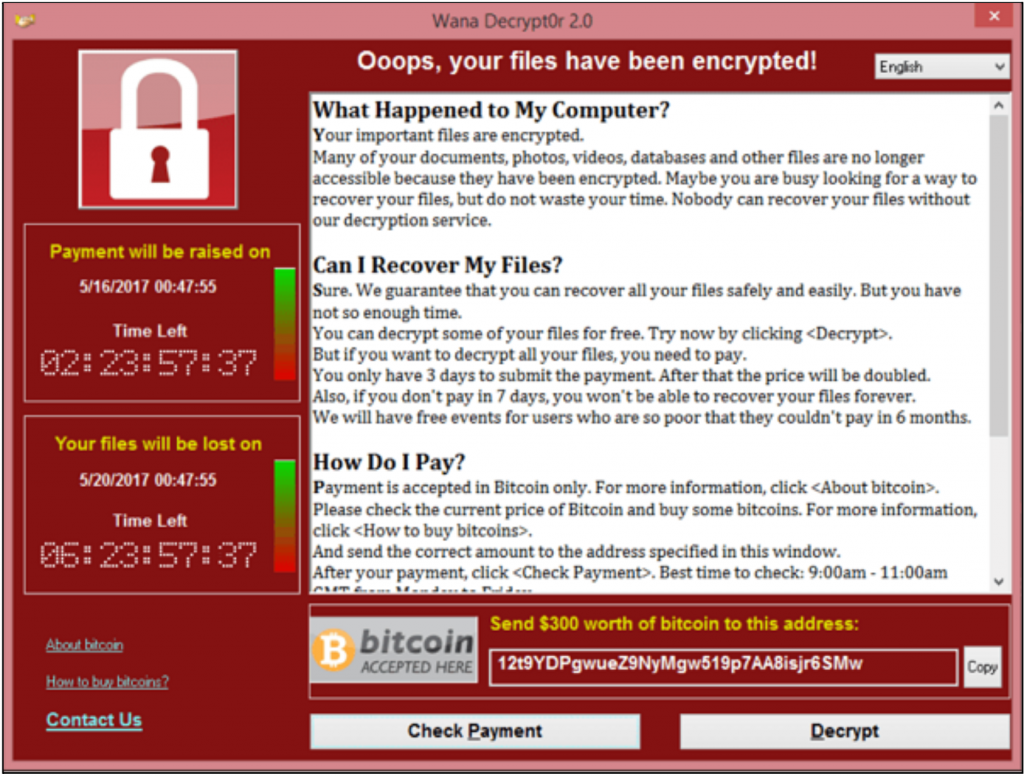
Ransomware is a form of malware that encrypts a victim’s files. In order to decrypt the system, it requires a decryption key, which is nearly impossible to guess. Once the system is encrypted, hackers usually place a message on the victim’s computer demanding that the victim transfer Bitcoin or other untraceable cryptocurrency to the criminals in exchange for the decryption key. Furthermore, hackers usually place a timeline on the ransom, and many raise the ransom amount if the original timeline is not met. Hackers can also download important data from the infected system and threaten a victim company to sell or release the information in the dark web.
The methods of intrusion vary, with some hackers gaining access to the system through phishing, while others look for vulnerabilities and security flaws in the system. Attacks could be targeted or random and may involve social engineering. Once hackers gain access to a system, they may spend a significant amount of time learning that system, gaining additional access, and downloading information. Many hacking teams also try to gain access to backup information, so that they can encrypt that as well and make the victim powerless to independently restore their own files.
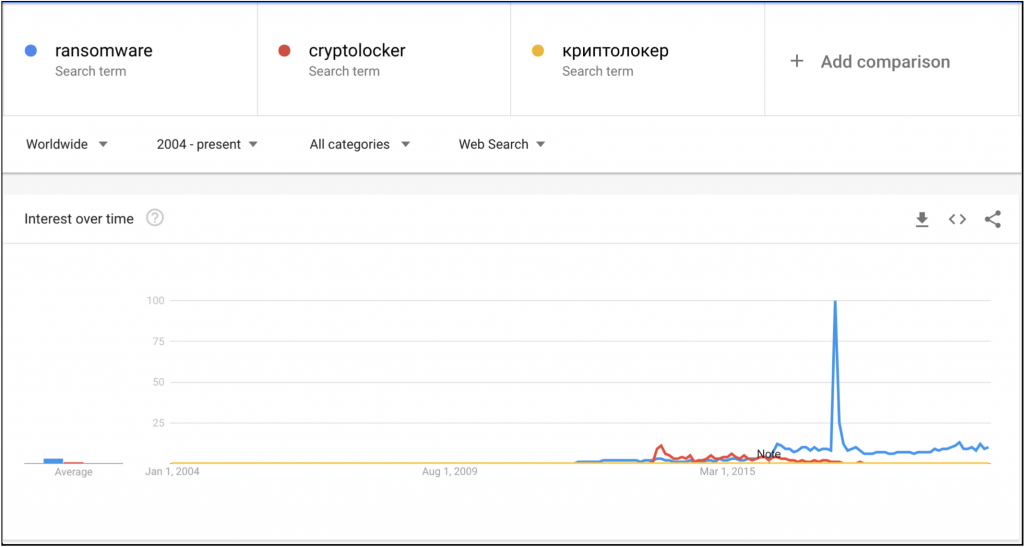
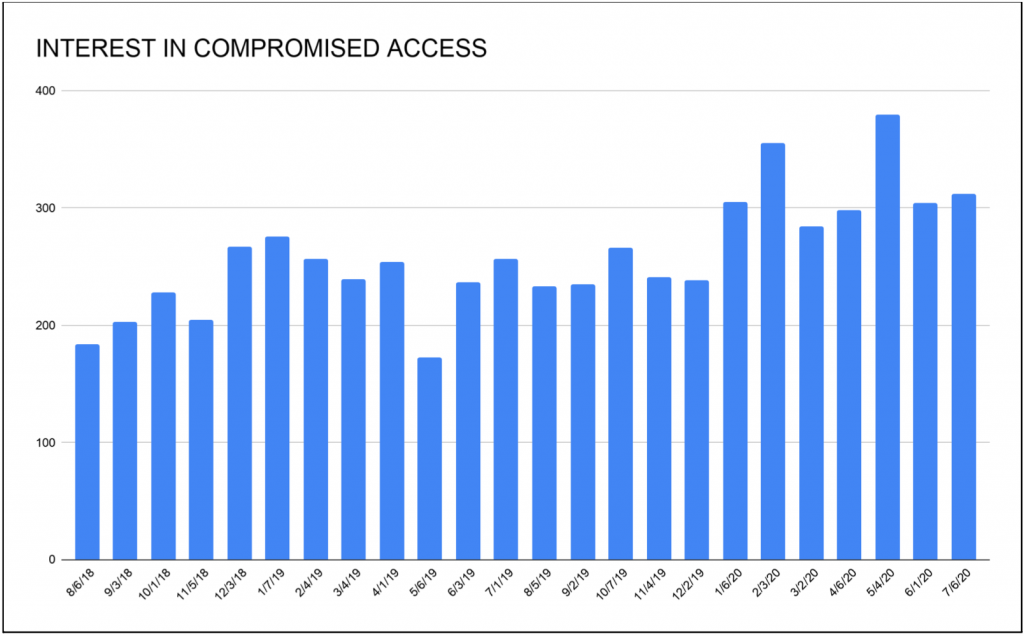
A keyword search on Google Trends for cryptolocker and ransomware revealed the level of interest associated with these terms. The peak activity lies in May 2017, which correlates with the initial WannaCry virus attacks. Following this, interest in cryptolockers continued to increase according to Google Trends, and it correlates with Gemini’s own assessment of these trends.

Dark Web Trends
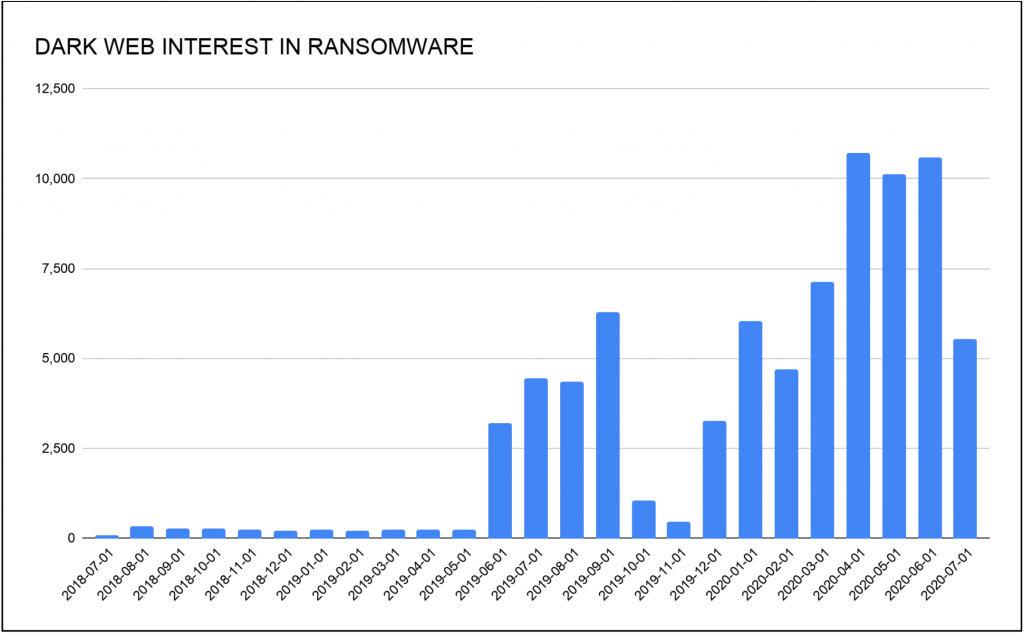
Gemini analysts have analyzed dark web forum mentions of the words “ransomware” and “cryptolocker,” as well as associated terms in other languages, and determined that over the last two years, interest in this type of malware has increased. Spikes in interest usually correlate with high-visibility hacks and large media exposure of such events. Prolific actors associated with this activity use the news media exposure to advertise their capabilities and to boast about their achievements, which in turn attracts more interest in their particular product.
It is also noteworthy that ransomware attacks against individual victims are far less common than they previously were. Cybercriminals now target corporations or other large institutions. This is because they can afford higher ransoms and often face significant operational disruption or liability concerns if they do not immediately pay.

The FBI’s Internet Crime Complaint Center (IC3) reports provide additional data associated with ransomware attacks. In 2017, IC3 received 1,783 ransomware complaints that cost victims over $2.3 million; in 2018, the IC3 received 1,493 complaints with losses of over $3.6 million; and in 2019, the IC3 received 2,047 complaints identified as ransomware with adjusted losses of over $8.9 million. Based on these statistics, the monetary damage increased four-fold from 2017 to 2019, and known attacks increased by 14%. However, these statistics should be noted for the rate of increase they describe, not for the actual numbers of ransomware attacks, since these incidents are grossly underreported. Additionally, many of the incidents that are reported are likely linked to individuals rather than businesses; a single successful attack on a business can net criminals a much more significant payoff.
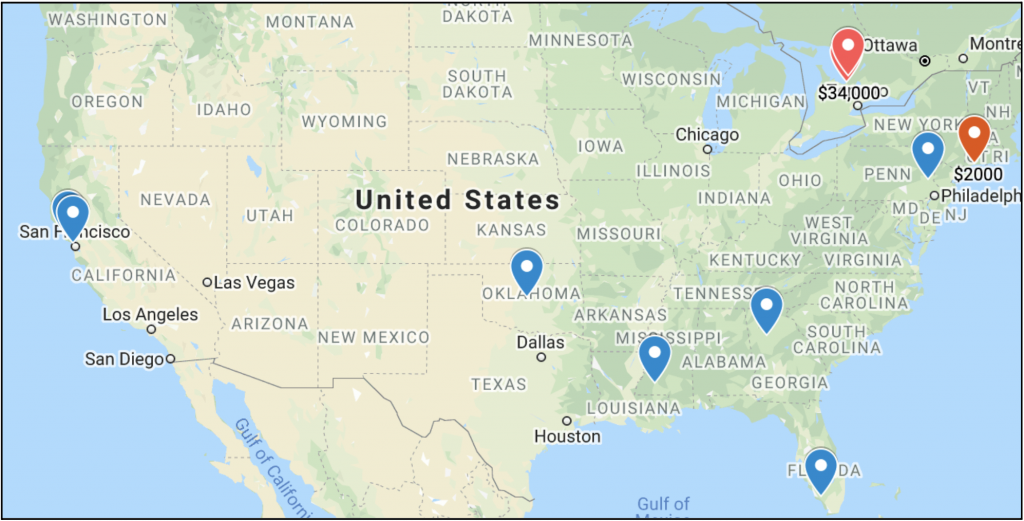
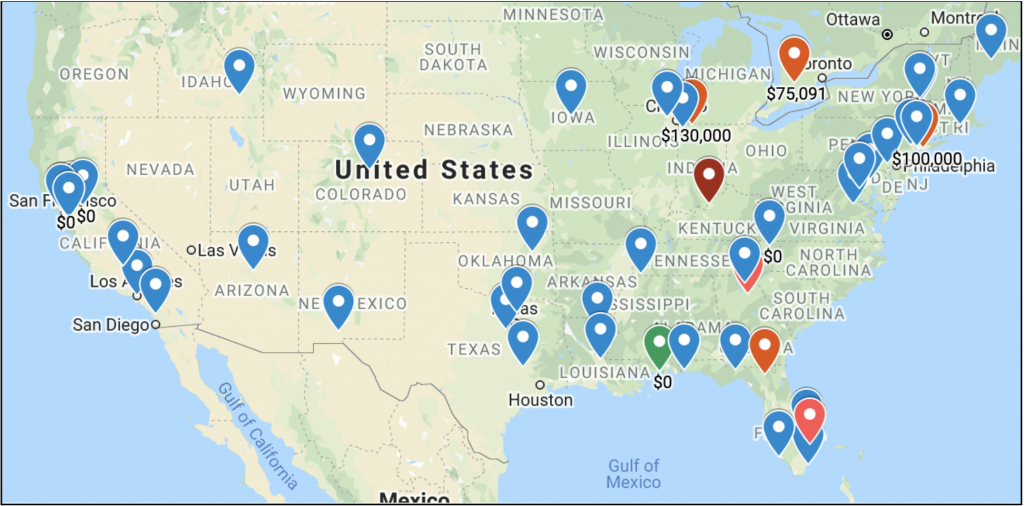
Gemini Advisory reached out to Simon Hunt, EVP of Cybersecurity at Mastercard. As part of a personal project unaffiliated with Mastercard, he put together a list of ransomware attacks on government entities, which are displayed in the screenshots below. Based on information that Hunt collected from open-source reporting, starting from 2019 there has been a steady increase in ransomware attacks on governmental organizations, cities, and even states. As such, in 2018 there were at least 10 ransomware attacks on cities, with a maximum amount of $40,000 paid to hackers. In 2019, the number of attacks had increased to a documented 51 attacks and the maximum payout to hackers was $600,000. Attacks are increasing exponentially, and as such, in the first two quarters of 2020, there were already 60 confirmed ransomware attacks on cities with a maximum payout amount of $2.6 million. It is important to note that in 2018 and 2019 these attacks were documented only in the United States, whereas in 2020, ransomware attacks on cities were recorded on five continents, primarily in Europe and the United States. It is worth pointing out that cities around the United States are also susceptible to other types of attacks, such as Click2Gov breaches, that Gemini covered in 2019. The various attack vectors employed in attacks against cities underline several gaps in their security measures.


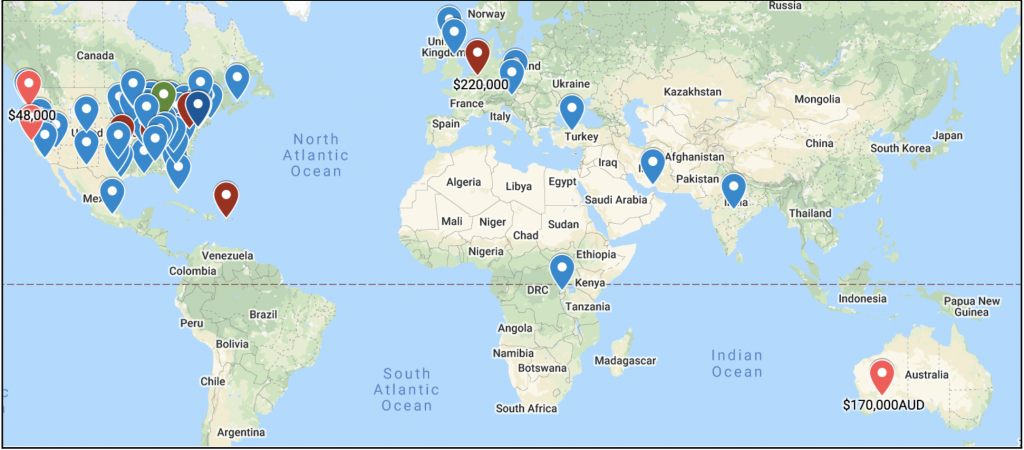

The number of attacks and payout amounts are usually underreported, both for the government and the private sector. According to a ProPublica article, private companies often do not release this information because it could scare their investors and drive down their stock prices. This includes both ransomware attacks designed to produce an actual ransom payment and attacks for espionage purposes. Furthermore, the ProPublica article claims that companies fear alerting law enforcement since that may start unrelated investigations into their business practices, or agents may discourage the company from paying the ransom.
Travelex, for example, suffered a ransomware attack by the “Sodinokibi” (AKA “REvil”) hacking group. This paralyzed Travelex’s online services, and while the company initially contested Sodinokibi’s claims to have obtained sensitive customer data, it resorted to pen-and-paper transactions immediately after the incident. Travelex eventually negotiated the ransom down from $6 million to $2.3 million and paid the hackers. Its parent company, Finablr, saw its stock price fall over 10% on the London Exchange in the 10 days following the incident. It plunged another 27% two weeks later when its majority shareholder committed more than half of the company’s stocks as security against its debt from buying Travelex. Due to compounding issues, including declining trust, financial difficulties, and the COVID-19 pandemic, Finablr is no longer trading on the London Stock Exchange and has seen its stock fall 93% this year. Travelex itself has recently been put into administration (i.e., bankruptcy).
An Emsisoft article calculated that in 2019 there were at least 966 government agencies, educational establishments, and medical providers affected by ransomware attacks in the United States, with potential damages of $7.5 billion. This data takes into account not only the ransom that was paid out to the hackers, but also the damages inflicted upon infrastructure, loss of business, the ability to conduct day-to-day activities, delays, and other issues associated with network disruption. Maersk, for example, suffered between $200 and $300 million losses despite having a backup copy of its data. This represents another difficulty with reporting these incidents, since different classifications of financial losses due to ransomware yield different numbers, which can be further distorted through partial reporting. Overall, underreporting creates a problem for investigating such attacks and hinders law enforcement’s ability to find the culprits or set appropriate defensive policies; this, in turn, incentivizes hackers to continue launching ransomware attacks.

Another issue compounding the problems of ransom-paying and underreporting is the role played by the cyber insurance industry. It is very often more profitable for a company to pay a ransom than to attempt to recover its files. Another ProPublica article states that “While insurers do not release information about ransom payments, ProPublica has found that they often accommodate attackers’ demands, even when alternatives such as saved backup files may be available.” When it is financially advantageous for each party (i.e., the hackers, the victim company, and the insurance company) for a cyber insurance company to pay the ransom, the cycle of crime becomes institutionalized.
This increase in attacks has also caused insurance rates to rise; an Insurance Journal article reported cyber insurance rates rising by as much as 25% in late 2019. Recent research by Deloitte indicates that stand-alone cyber insurance policies are becoming more widespread as the news of more and more midsize and large companies are falling victim to these ransomware. According to the same research, net written premiums equaled almost $2 billion in 2018. However, the significant increase in attack frequency since 2018 would suggest that in the past two years, these premiums have grown accordingly. According to 2015 Allianz estimates, the cyber insurance market is forecasted to grow by over $25 billion by 2025.
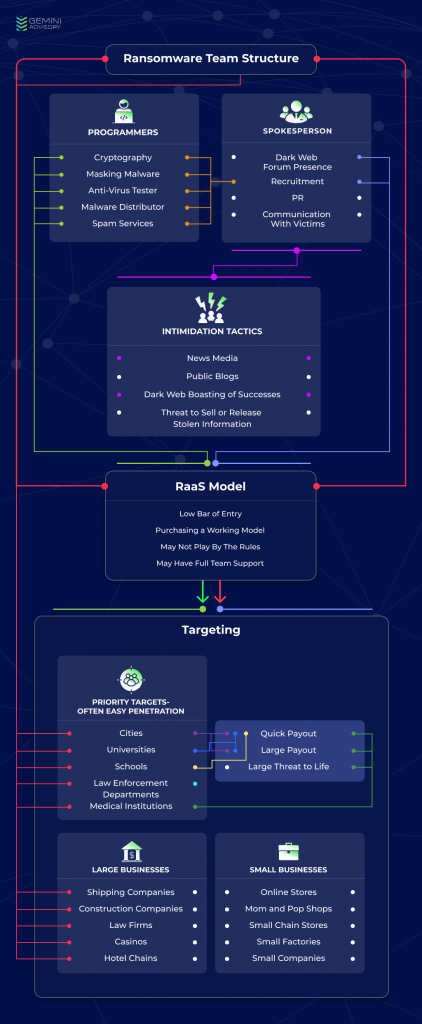
Most modern ransomware attacks require a team of cybercriminals in which each member is assigned a specific role. One way that a team can acquire malware is by purchasing source code from other cybercriminals, and then modifying it for its own needs. A technical analysis conducted by Secureworks indicated that software used by the Sodinokibi team has striking similarities to “GandCrab” ransomware, which could indicate that Sodinokibi includes the same hackers responsible for creating GandCrab, or that Sodinokibi simply used the source code from GandCrab to create its own malware.
In order to create the malware itself, the team requires a programmer proficient in cryptography who creates a specific crypto algorithm for the malware. Additionally, the team will need a programmer who can ensure that the malware is hidden when it is inside the infected system and remains undetected by antivirus systems. The team also requires a tester to test the malware against the popular antivirus software and endpoint protection systems. It is important to note that malware used for ransomware is part of the Trojan virus family, and infection most commonly occurs by opening an executable file from an email (potentially a spam email), or by finding a vulnerability inside a network. Depending on the attack vector, the team may require specialists to distribute the malware. This could include specialists in social engineering, spam services, web designs, or network security.
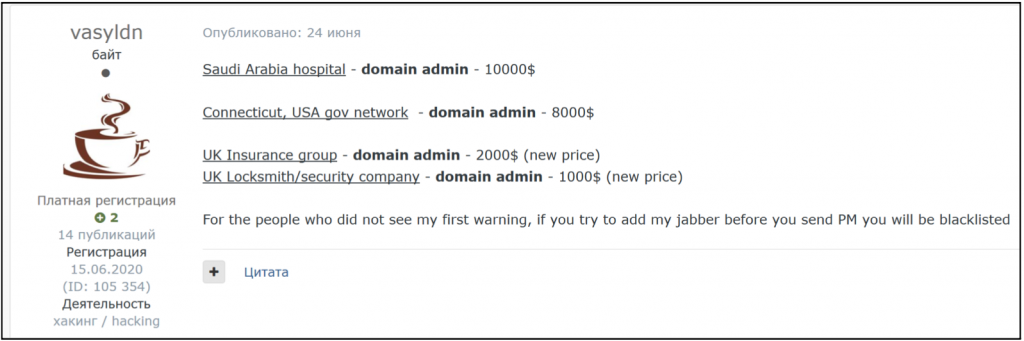
The team also requires a spokesperson who will be the voice of the team. A spokesperson usually has a presence on the dark web forums, where they can advertise for the team and boast about their achievements. Their boasts can serve to elevate the group’s status, recruit new members, or encourage other dark web members to offer them access to systems or vulnerabilities. Additionally, the spokesperson could communicate with the victims and negotiate for the ransom.
Assembling a team and creating custom malware is a complicated and time-consuming task, but criminals can also use a RaaS model to conduct these types of attacks. Gemini analysts have identified an increased interest in this type of service in the dark web in recent years. The low technical knowledge required to utilize RaaS attracts a wide range of cybercriminals, and as such, even novice cybercriminals can launch ransomware attacks. Extensive media exposure and ransomware teams’ boasts about their successes in the dark web create a lucrative environment for those looking for new ways to generate revenue. Those that offer RaaS services usually emphasize making their product user-friendly and providing support to those who need it. Essentially, it works as a rental, with a group of RaaS hackers renting malware to cybercriminal customers with varying levels of involvement. Some may offer just the malware and the decryption keys, while others offer a full package.
A full package may include an admin panel, which allows the cybercriminal customers requesting RaaS to monitor their victims, the progress of infections, and the payout information. Additionally, some include a support center that allows the cybercriminal customers to contact the RaaS hackers for technical support. This support center can also act as an intermediary between the cybercriminal customers and their victims to facilitate a ransom payment. The costs of the use of such services depend on the package that the user chooses, which could include a percentage of the payoff amount.

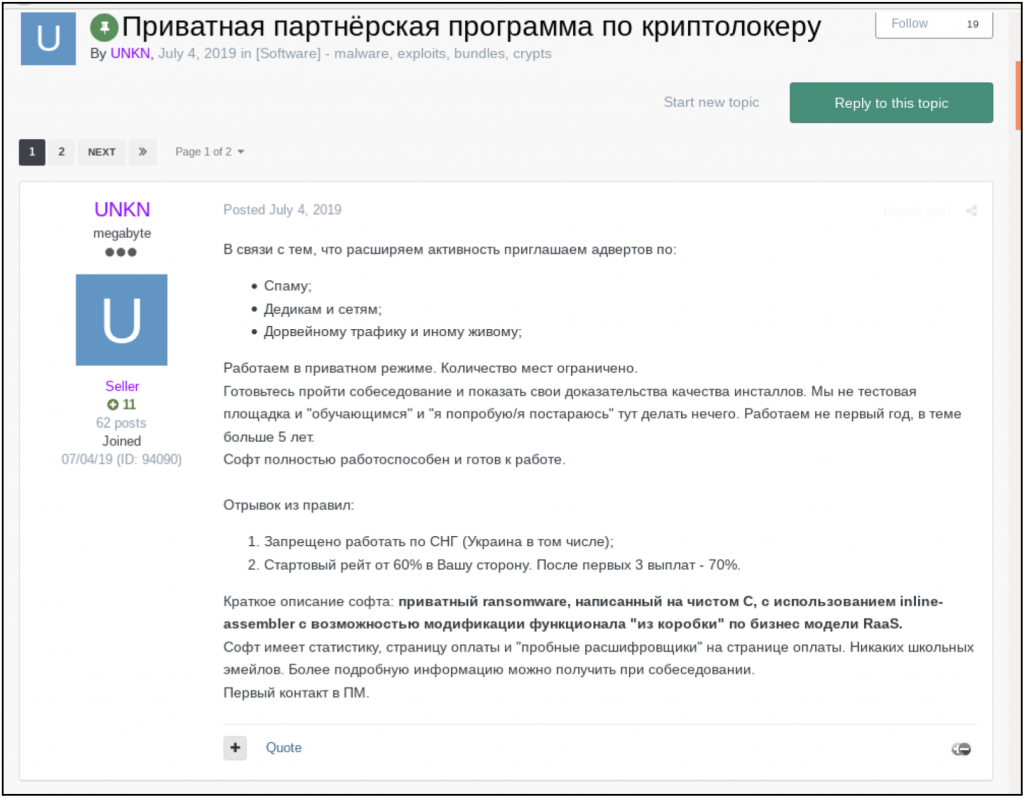
Sodinokibi has made the news in the past year due to its high-value targets and high payoff amounts, and is considered to be one of the most well-known and prolific ransomware actors in the field. A dive into the dark web forums reveals that the group was recruiting members on the forums and set requirements for joining the team. A known member of underground forums operating under the monikers “UNKN” and “Unknown” on top-tier Russian-language dark web hacking forums appears to be the public face of the organization and frequently boasts about the team’s successes. KrebsOnSecurity published an article identifying a possible connection between GandCrab and Sodinokibi, as mentioned above, and alleged that UNKN may have been one of the principle coders for GandCrab.
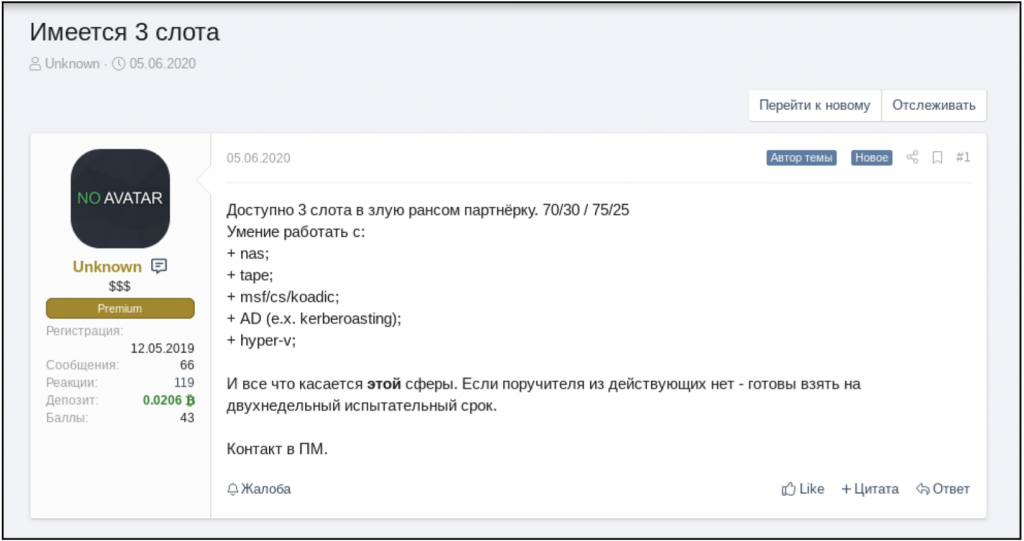
Additionally, UNKN posts recruitment ads in which they list the requirements for new recruits. As seen in the image below, on July 4, 2019, they were looking for specialists in spam, Remote Desktop Protocol (RDP) access, and doorway traffic. UNKN clarified that they were searching for experienced individuals to interview for the position. They also list two of their key rules. First, they cannot target entities located in the Former Soviet Union (FSU), which is one of the main unwritten rules of the Russian-language underground overall. Second, the initial split gives the recruit 60% of the payout, and after three successful campaigns, the partner’s share would increase to 70%. The hiring process remains ongoing; on June 5, 2020, UNKN created a new ad for three open slots in their team and listed the requirements for the candidates: required proficiency with NAS (Network Attached Storage); tape (magnetic tape data storage); MSF (Microsoft Solutions Framework) / CS (Certificate Service) / Koadic (COM Command & Control); AD (Active Directory), for example Kerberoasting; Hyper-V (Microsoft virtual machine).


As was mentioned above, there are sometimes rules for operating under the RaaS business model. The malware creators can dictate certain rules since the malware is their brand and they may want to garner a certain image. If their product was used to encrypt a target system, and the cybercriminals refused to decrypt the system even after receiving a ransom payment, this could tarnish the malware creators’ reputation not only in the civilian world but also in the cybercriminal underground. The next company to be infected with this malware may be hesitant to pay the ransom since decryption is not guaranteed. This, in turn, lowers the desirability for this ransomware in the dark web since cybercriminals are less likely to use a malware that deters its targets from paying. Thus, certain teams exercise control over whom they allow to use their malware, while others are less stringent.
It is important to note that despite their appearance, not all ransomware attacks are centered around payout. During the COVID-19 spike, a medical research company was attacked by Sodinokibi malware, prompting cybercriminals on the forums to debate the morality of targeting medical institutions, especially those that are on the forefront of finding a cure to end the pandemic. Member UNKN disclosed that their customer used the ransomware as a cover-up in order to conduct corporate espionage rather than for a payout. While this answer may not be a satisfactory response to the moral debate, it underscores the multiple motivations and intentions of cybercriminals using ransomware. As well as receiving a ransom payment or conducting corporate espionage, it can also be used by nation-state or extremist groups for direct attacks on enemy infrastructure. For example, a recent New York Times article indicated that the Russian government used an advanced persistent threat (APT) group to attempt to steal coronavirus vaccine research from Western nations. Russian-linked hackers have often used ransomware to disguise more destructive intentions. In these scenarios, it is unlikely that the victims would get the decryption keys even after they pay the ransom.
Some criminal groups use public relations In order to intimidate their victims into paying a ransom. This may include boasting about their successes on dark web forums, writing public blogs, or circulating their media exposure. A more straightforward means of intimidation is to threaten to sell or publicly release the encrypted information, as was the case with Travelex and the law firm Grubman Shire and Sacks, which the hackers claimed contained sensitive information pertaining to President Donald Trump.
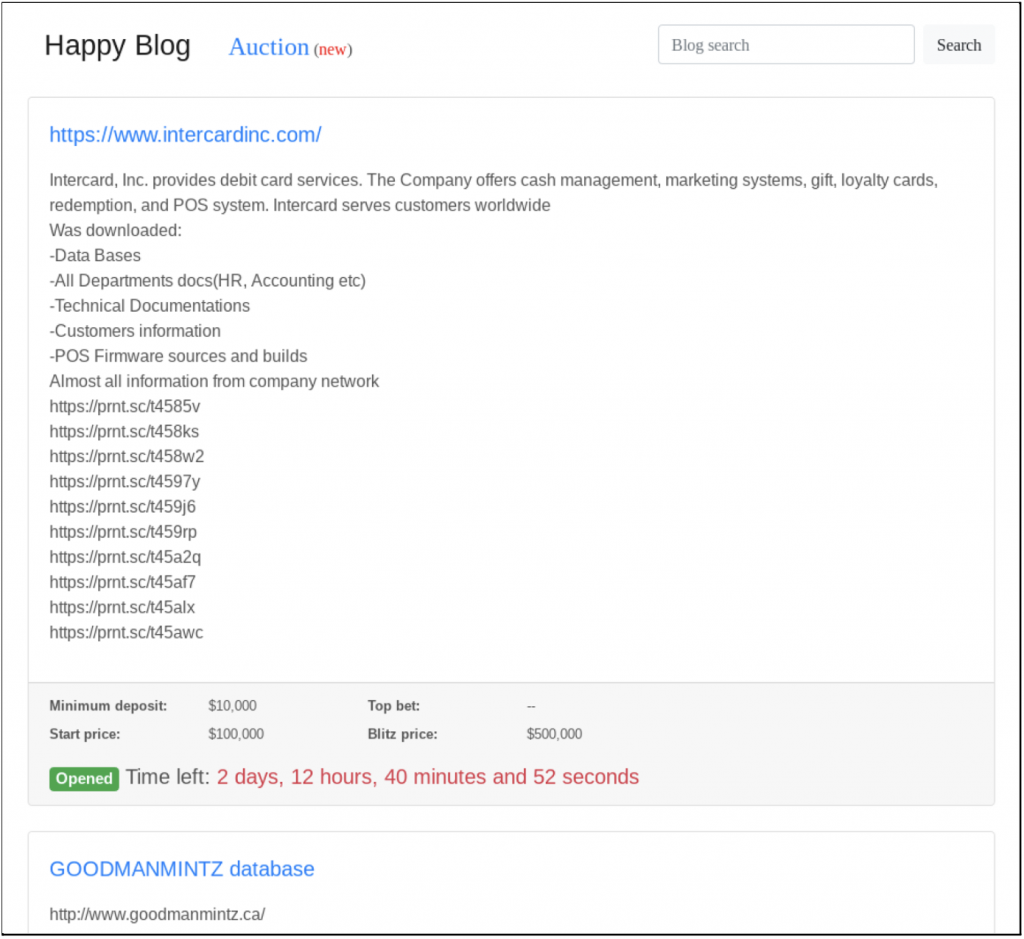


As was described above in the Operations and Hacking Teams section, there are different ways in which criminals can gain access to computer systems. One method is purchasing access on the dark web forums from individuals who specialize in gaining such access (whether accidentally or intentionally). Additionally, cybercriminals could broadly search the internet to find networks vulnerable to the attacks. These weaknesses could be due to unpatched software with a known vulnerability. Hackers could also conduct brute-forcing (credential-stuffing) attacks. Brute-forcing attacks use specially designed software to automatically pair known generic usernames and passwords, such as “admin” and “password.” Most computer equipment is sold with generic login and password information, and unless the owner updates these settings, hackers can easily gain access.
Once criminals obtain access, they may offer it for sale in the dark web for interested criminal entities, such as ransomware teams. While interest in obtaining compromised access has not significantly increased in the underground economy, cybercriminal buyers have recently shifted away from using this access to steal documents, and instead leverage access to launch ransomware attacks.

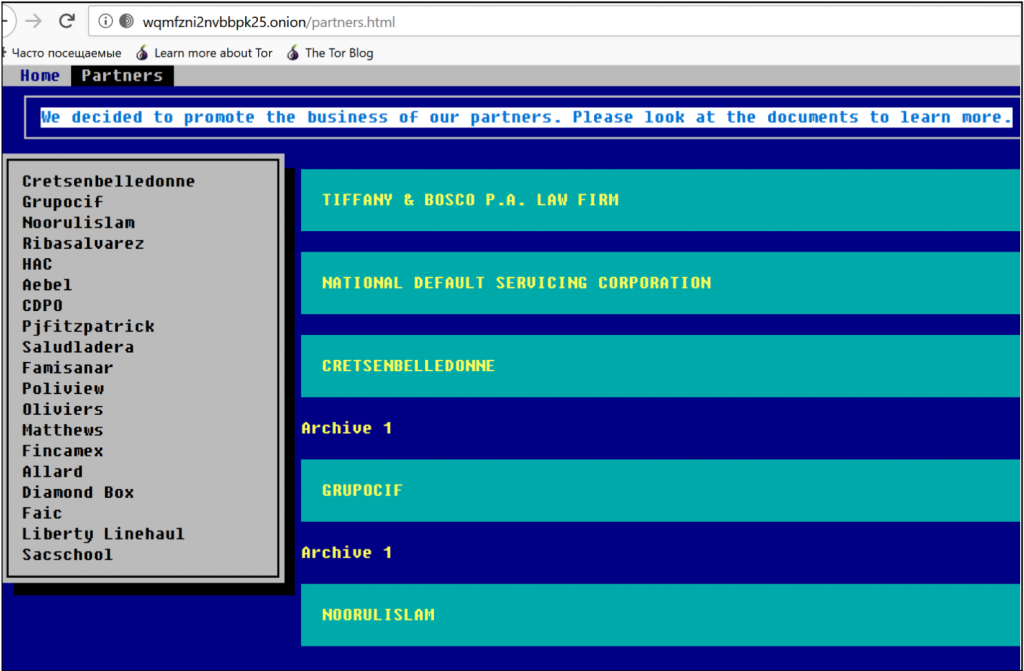
Another method that hackers can use to access a target system is through compromised RDP or by the use of web shells. Both can be purchased in underground marketplaces, one of the most notorious of which, xDedic, was shut down by the FBI in early 2019. That marketplace allowed its users to search for compromised computer credentials based on various criteria so they could pinpoint their attacks. Once cybercriminals have access to RDP, they can access the network with which this RPD is associated and install ransomware. Tyler Hudak, an incident response lead from TrustedSec, created a honeypot experiment in which he set up an RDP with default settings and basic login credentials (user: “payroll” / password: “password”). His system was probed thousands of times over the nine-and-a-half days that it was online, with many successful penetrations. The first attacker that got into the system installed ransomware immediately upon access. Even though xDedic was shut down, other RDP marketplaces took its place, as is common in the dark web, so there are still plenty of ways to acquire these accesses.
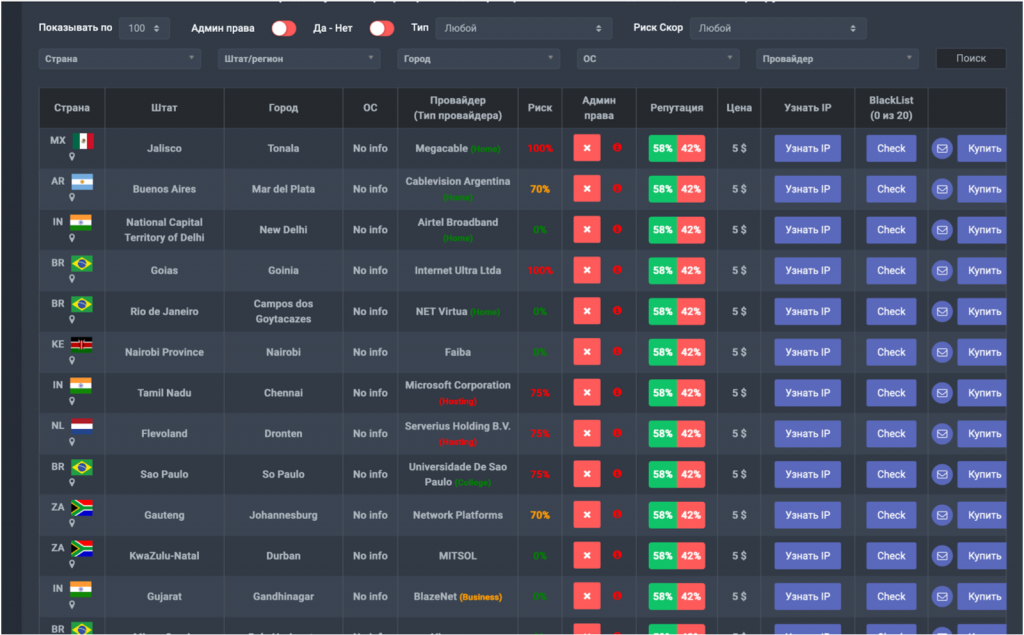

Access to various organizations can be found across the dark web. The price of access is proportionate to criminals’ ability to monetize that access; access to a company with large resources generally correlates to a higher ransom, and thus a higher price for access. A few of offerings on a hacking forum were listed as follows:
These examples include several recent postings. Usually access of this type sells in a short time, such as a week or even the same day as the posting. For example, sailormorgan32’s June 28 ad was pulled on July 3. These only indicate access sold on the forums, and there are likely many additional sales conducted privately among tighter-knit hacking groups with long-standing partnerships. Ransomware teams with individuals dedicated to obtaining access to target systems can avoid the forums altogether while conducting high-profile and lucrative attacks.
While it may be possible to recoup financial losses or reputational harm, many institutions are not willing to risk human life. More and more often, hackers target medical institutions due to their inability to negotiate. Cybersecurity company Recorded Future reported that through 2019 there were 134 publicly reported ransomware attacks against healthcare providers, and in 2020 there were already 26 ransomware attacks against US healthcare providers as of July 16. Many modern hospitals rely on computer systems in order to run their daily operations, including distributing medications to patients, which are controlled by special cabinets that use computer systems to operate their locks. Naturally, most medical charts are stored on computers and many medical workers rely on specially designed medical programs that assist in diagnosing and treating patients. Additionally, modern surgeries are performed with the assistance of robotics, which is becoming more prevalent in the modern world. Ransomware could completely paralyze hospital operations and could put patients at risk if the doctors are unable to retrieve the medication that they need in a timely manner, or it could freeze a system designed to retrieve data and detect anomalies, or disrupt lab systems that perform analysis, or perhaps even force a robot offline during surgery. All of these disruptions could be life-threatening, meaning that hospitals are in no position to negotiate with the hackers and must try to get their systems back online as soon as possible, which could mean a big payday for the criminals.
Dark web forums also sell access to medical facilities’ systems, including RDP access to a hospital or an organization that handles medical data. This has become popular because ransomware is particularly effective against hospitals. They vary between large and small companies with pricing often corresponding to the organization’s perceived ability to pay. A few examples are as follows:

Now that the world has fallen victim to the COVID-19 pandemic, many companies heavily rely upon employees working remotely. This creates network security problems that prove difficult to mitigate. In the modern world, individuals have a large number of gadgets linked to their home network. Cybercriminals could breach those gadgets through various vulnerabilities and then pivot to access the home network. Even if a work computer system is secure, vulnerabilities in home networks are harder to avoid, which opens the door for a new set of problems. This provides a new attack surface for hackers interested in breaching corporate systems in order to conduct ransomware, as well as other illegal activity.
The ransomware threat no longer focuses on individual users since almost all ransomware attacks now target businesses, corporations, government entities, and hospitals. In the past, the risk was that an individual might have lost personal or sensitive content from their computer (e.g., cat photos), whereas human lives could now be at stake. The low level of technical expertise necessary for engaging in ransomware activities is alarming. Criminals have created an easy-to-use platform that lowers the barrier-to-entry for novice and low-level hackers. This has led to mass proliferation of ransomware. Alongside newly desirable ransomware insurance policies, it has institutionalized the cycle of crime and payment and has made ransomware a new cost of business in the modern world.
In the past, only a few well-organized teams conducted these types of attacks and abided by certain rules, such as reliably providing decryption keys after payments were made. Now that these types of attacks are gaining popularity, there are no guarantees that the old rules will be followed. Additionally, many ransomware programs are now designed to permanently encrypt the data or even erase the content if payment is not made within a certain period of time. If the victim does not pay in time, if the hacker does not clearly communicate the timeline, or if a novice hacker does not provide the decryption keys, then even after the payment is made, it may be impossible to recover the system. This, along with threatening messages sent to victims warning against alerting law enforcement or trying to decrypt their systems, and even the timeline of payment, can scare victims into submission. The victim risks not only losing all of their information, but also having it distributed across the dark web.
A few precautions could minimize the risk of a ransomware attack. One of the basic rules of modern network security is to change login information on all new systems so that it is not generic, preventing criminals from easily guessing the logins. Another step is to ensure that all the software is up to date and all vulnerabilities are patched. An organization should have good end-user training, since many of these attacks rely on phishing emails. Proper training includes instructing employees to check the source of the emails that they receive and being mindful about opening any email attachments. Finally, it is crucial to keep backups of all files in the system, and to avoid keeping the backups on the main network, so that they cannot be compromised in case of an attack. Although many of these items are normally a part of any institution’s security measures, it is important to do frequent reviews of systems and employees, as these fairly simple steps could significantly lower the risk to the institution.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate assets targeted by fraudsters and online criminals in real-time.