
While cybercrime has dramatically increased in the past several years, Card Not Present (CNP) fraud, in particular, has become far more prolific as the world shifts towards online commerce and digital transactions. This type of fraud, which encompasses schemes that use stolen payment card data to purchase goods and services online, has been devastating to retailers, according to analysts at Juniper Research. By 2023, Juniper projects that CNP carders will have siphoned a total of $130 billion from merchants’ top line over the trailing five-year period modeled by its 2019 report. Additionally, global business lockdowns and the overall disruption of brick-and-mortar retail caused by the COVID-19 pandemic have further migrated card fraud activity to CNP vectors.
According to August research from payment data provider ACI Worldwide Data, year-over-year, global e-commerce transactions rose by 19% in July 2020. While the overall volume of fraudulent transactions has slightly declined, ACI data also revealed a 4.4% increase in the value of fraudulent transactions compared to the previous year.
Additionally, ACI executive vice president Debbie Guerra said: “Fraudsters are targeting higher value items like electronics and luxury brand names, especially within newer channels such as curbside pick-up and in-parking lot pick-up.”
Contrary to popular belief, however, effective card fraud, or carding, entails much more than the theft of card data and traditional personally identifiable information (PII) from victims. This is because sophisticated retailers like Amazon, Walmart, and others secure their e-commerce payment gateways and networks with increasingly robust anti-fraud systems.
Some popular fraud-monitoring solutions include Iovation, Riskified, Kount, Bolt, Stripe Radar, Sift, Radial, and Seon. These regulatory technologies (regtechs) use consortium data harvested from merchant payment networks to authenticate card and account holder data. They authenticate user and device identity by analyzing a vast metaverse of digital fingerprints in real time.
Some common examples of the “fingerprints” logged by these systems include IP data, browser information, device, screen dimension, time zone, language settings, and the browser plugins installed. Other more granular fingerprints include the video and memory cards hardwired into the device, the WebGL debug vendor, serial numbers, firmware, and the servers known to host online connections for that user.
All told, there are over 100 user and device fingerprints that anti-fraud systems can cross-reference to authenticate transactions. Apart from these fingerprints, behavioral analysis of social networks, third-party cookie checks, website clicks, and touchscreen behavior comprises a secondary component of anti-fraud monitoring systems.
This data is logged via a consortium model that aggregates flows from merchant terminals and recirculates consumers’ unique digital fingerprints throughout payment networks. Amazon, for example, benchmarks customers’ digital fingerprints against transactions buyers have executed with other online merchants.
Beyond regtech solutions, other merchants have just migrated outright to the modern 3-D Secure 2.0 digital payment standard. Initially piloted in 2017, 3-D Secure “creates an authentication data connection between digital merchants, payment networks, and financial institutions to be able to analyze and share more intelligence about transactions,” according to Visa.
Given the poor user experience that plagued the first iteration of the 3-D Secure standard, however, merchants have been slow to adopt the upgrade. Small merchants have proven particularly averse to adopting expensive security standards. While Frictionless 3D Secure 2.0 Technology depends on the provider and volume of the transaction, it ranges between $0.20 and $0.50 per transaction. Regardless, anti-fraud systems are clearly not a panacea for the increasing sophistication of savvier carders.
Gemini Advisory researchers combed the most exclusive hacker forums in the Russian-language dark web. By monitoring historical posts, the team discovered a flourishing commercial marketplace for anti-fingerprinting software that can hack the monitoring schemes employed by leading regtech vendors.
Gemini analysts unpeeled the onion of dark web forums to uncover actionable intelligence about the tricks of the modern carding trade. Some of the most popular solutions touted by the cybercriminal underworld include “Antidetect” by “Byte.Catcher,” “Linken Sphere” by “Tenebris,” “Genesis Plugin” by “GenesisStore,” and “Antidetect” by “Dr. Cert.”
However, forum chatter reveals that the effectiveness of these applications varies from carder to carder. While some scammers consider the leading anti-fraud systems to be “practically impregnable,” others claim to possess the operational security (OPSEC) needed to bypass merchant payment firewalls.
In the end, Gemini research suggests that successful carding hinges on the technical proficiency of the cybercriminal using these anti-fingerprinting tools. In other words, the carders actually have to be hackers. In the analyses below, Gemini will discuss some of the most trafficked fingerprint-spoofing browsers and review their effectiveness based on carding community chatter from the dark web.
Antidetect by Byte.Catcher is the most infamous fingerprint-spoofer, Gemini researchers found. This application owes its notoriety to a series of news stories authored by cybersecurity journalist Brian Krebs in 2015.
At their core, Antidetect and competing applications are tools for “creating browsers with different configurations,” according to Antidetect’s website. “A configuration, or a config, is a collection of javascript files copied by a special method from real browsers. Each new browser will look like a browser from the config, and have unique Canvas prints, WebGL, fonts,” says the website’s marketing collateral.
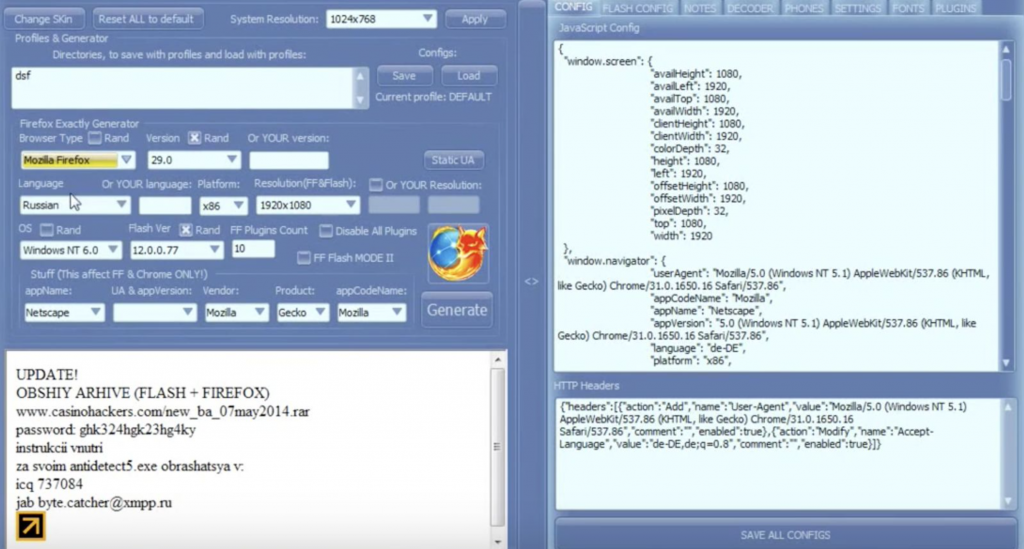

Image 1: The interface of Antidetect by Byte.Catcher.
Just like the Tor browser, Antidetect also runs on Mozilla’s Firefox codebase. The software even enables users to simulate the iOS configuration from their desktop device. Today, the price for Byte.Catcher’s annual software license ranges from $600 for the standard 7.7 version, all the way up to $2,999 for Antidetect 8, which Byte.Catcher calls: “the best fingerprint-bypass tool its [sic] like to print your own money.” This threat actor accepts only Bitcoin as a payment method.
Antidetect’s website stated that its core product features enable users to modify the following:
In 2015, Krebs raised mainstream awareness for the Antidetect software suite within the information security (infosec) community with this article, in which he linked to a sales video showcasing an Antidetect demo. In the demo, an unidentified user provided viewers with a card-fraud walkthrough.
Beyond Antidetect, Gemini intelligence frequently encountered posts citing carders’ preference for Linken Sphere.
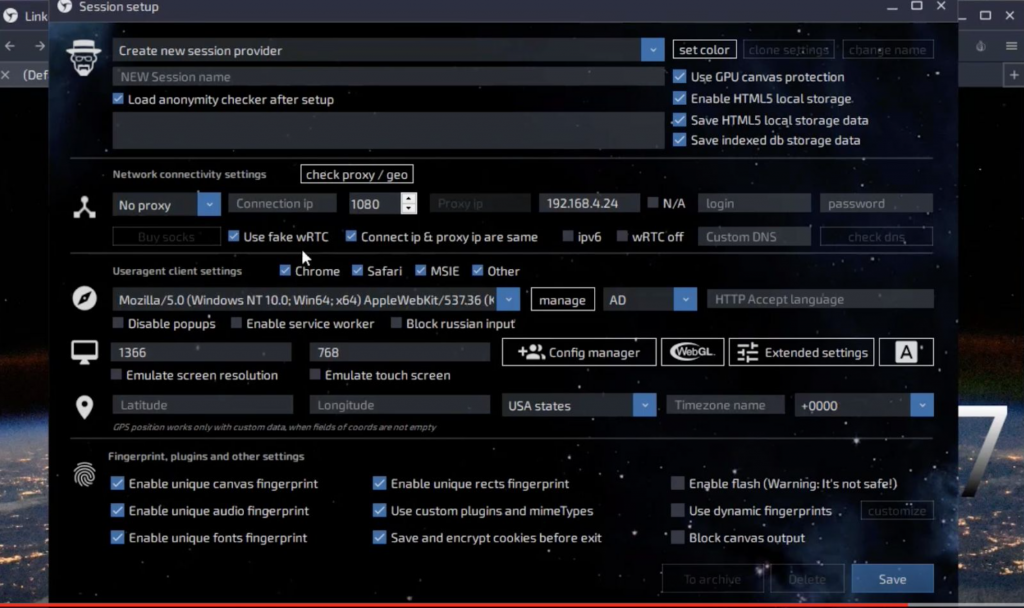

Image 2: Linken Sphere’s interface.
Engineered by rogue developers from the “Tenebris” group, the Sphere browser “is equipped with protection and fingerprint substitution systems (GPU, Audio, Canvas, Plugins, Fonts, ClientRects, Ubercookies),” according to the developer’s website.
“Nobody will be able to recognize the configuration of your hardware if you work with Linken Sphere – it will protect you from any identification attempt,” says the site’s marketing collateral.
In a 2019 report on the anti-fingerprinting ecosystem, Kaspersky wrote that “Sphere is a fully functional browser with advanced fingerprint configuration capabilities, automatic proxy server validity testing and usage options, etc. It even features a user activity emulator – cybercriminals can program it to open the desired websites.”
Additionally, Sphere offers a much deeper ability to configure fingerprints than other antidetects. Most of its parameters are customizable, enabling cybercriminals to tailor the fingerprint to the precise profile needed to mimic their target.
Sphere is also more affordable than Byte.Catcher’s Antidetect and priced between $100 for a one-month subscription or $900 for a year-long user license. Just like Byte.Catcher, Tenebris also mandates payment exclusively in Bitcoin.
According to a 2018 post from dark web forum user “nightraven,” they used Sphere for nearly a year and were able to steal money from various online retailers. It is unclear if the methods used two years ago are still effective today, however.
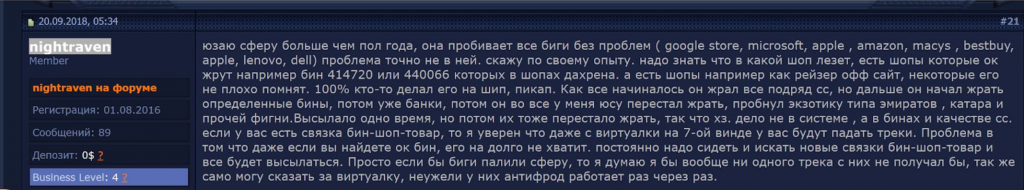

Image 3: Russian-language Sphere review from nightraven on September 20, 2018.
“I’ve been using the sphere for more than half a year, it works well with (google store, microsoft, apple, amazon, macys, bestbuy, apple, lenovo, dell) so the problem is not with the sphere. I will say from my own experience. you need to know what kind of shops work best with what bins, for example bin 414720 or 440066 which are in abundance work well with most shops,” quoth the nightraven.
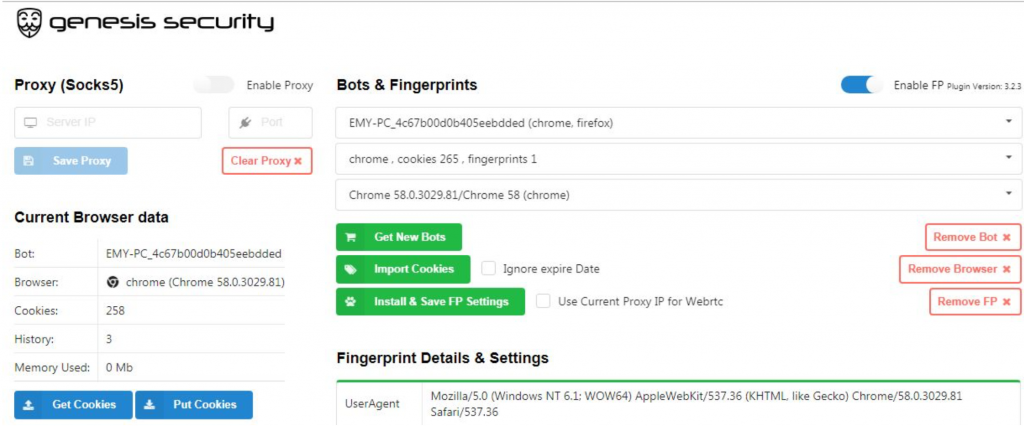

Image 4: Genesis Plugin interface.
Another popular anti-fingerprinting solution is the Genesis Plugin by developer Genesis Store. In 2019, Kaspersky called Genesis Store the “biggest marketplace” for stolen fingerprint data. Unlike Sphere and Antidetect, however, the plugin is not a fully functional web browser.
Launched in November 2018, Genesis Store is an invitation-only cybercriminal marketplace for stolen digital fingerprints. As of this writing, it offers 306,000 stolen bot profiles. These bot profiles include: Browser fingerprints, website usernames and passwords, cookies, and payment card data. Prices vary from $5 to $200 per profile.
After purchasing a Genesis Store fingerprint, the marketplace provides customers with a Chrome extension that enables them to apply the stolen credential to their browser and impersonate the hacked user.
With just a click of the mouse, the plugin enables carders to install stolen digital profiles into their browsers and assume their targets’ identities. But in order for the scheme to work, the carder must first connect to a proxy server that lists an IP address from their target’s location. From there, they can bypass the anti-fraud filter’s authentication systems and transact as a verified user.
However, Genesis’ monopoly over the cybercrime market economy – trafficking 90 percent of all stolen data at its height – may have been disrupted by a patch to the Chrome 80 upgrade in February of this year, according to ZDNet. This browser upgrade disabled the “AZORult” malware that allowed hackers to swipe virtual prints from Chrome users with impunity. These Chrome prints represented the bulk of the marketplace’s fingerprint inventory.
By switching to the AES-256 encryption standard to hash user’s Chrome passwords, Google has thus crippled this malware strain’s ability to extract passwords. “While last year Genesis was seeing a steady influx of 18,000 new stolen fingerprints being added to the site on a daily basis, this number has now gone down 30 times to roughly 600 new entries,” as of late February, writes ZDNet.
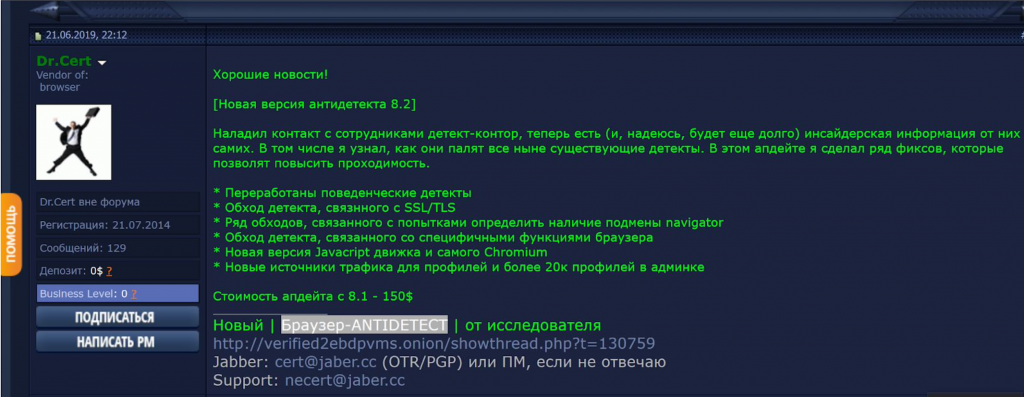

Image 5: Dr.Cert hawks their wares in Russian on a dark web forum on June 21, 2019.
Another finger-print evasion application uncovered by Gemini’s dark web sleuths is the Antidetect tool by a user operating under the alias Dr.Cert on a top-tier Russian-language forum. Retailing for $5,000, this service is also the most expensive amongst its peers. But at the time of Gemini’s research, Dr.Cert only offered 40,000 unique fingerprints, far less than the Genesis Store’s bot inventory before the Chrome 80 upgrade.
The unique advantage touted by Dr.Cert’s Antidetect is that this user claims to have insider information from working at an anti-fraud company. In a separate post authored in February 2019, Dr.Cert wrote that they had seven years of hands-on experience working in the anti-fraud field and “script reversing.”
They also described five principles for duping anti-fraud systems and revealed a semi-proprietary JavaScript template that these types of platforms use to authenticate virtual fingerprints.
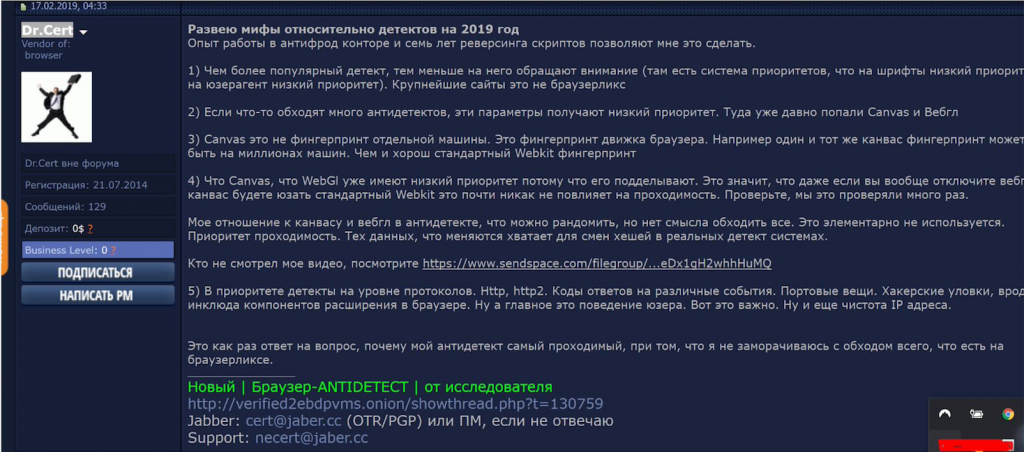

Image 6: ‘Dr.Cert’ explains five pillars of anti-fraud systems in Russian on February 17, 2019.
Some gems offered by Dr.Cert include:
Because of these factors and others, Dr.Cert said that their “antidetect is the most passable, despite the fact that I do not bother with bypassing everything that is on the browser.”
Nifty software aside, Gemini research revealed that anti-fraud systems largely catch only inexperienced carders (“noobs” or “schoolchildren,” per the forums), which comprise the vast majority of them. As for professional cybercriminals, these systems are only a temporary hindrance.
Nevertheless, the general consensus is that these anti-fingerprinting browsers are all “lousy,” according to a Russian-language technical review of Sphere and three other competitors: “AntBrowser,” “Aezakmi,” and “Indigo” (also known as “Multilogin”).
However, despite being generally underwhelmed, the review from affiliate marketing news site CPA[.]RIP identified Indigo as the best antidetect tool, despite its inability to mimic a “native system font.” Gemini research on a top-tier Russian-language forum recovered a 2018 post in which user “molotovkeyt” recommended the tool and attributed its authorship to Estonian hackers.
But, highlighting the enduring resilience of anti-fraud systems like Iovation, for example, a forum member, “derkoba,” noted that most carders’ OPSEC is still no match for Iovation’s defenses.
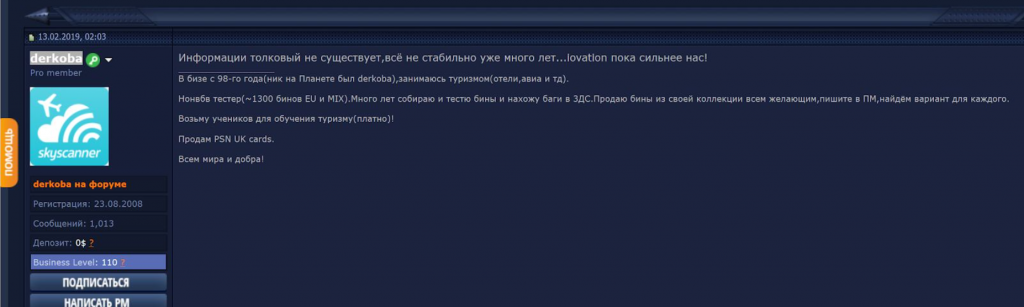

Image 7: Hackers are no match for Iovation, says derkoba in Russian on February 13, 2019.
Similarly, top-tier cybercrime forum member “traqtor,” posted last year about how antidetects sold online were a “waste of money.”
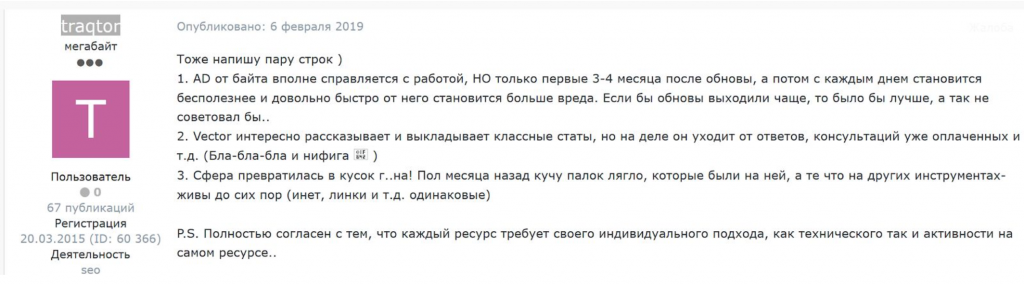

Image 8: Forum user traqtor critiques commercially available antidetects in Russian on February 6, 2019.
traqtor noted that these tools can only increase the speed of work, but they do not improve authentication. However, traqtor did mention that the calculus changes when a carder possesses an account with robust logs, but that data set has to be very specific to the user targeted for impersonation and theft.
Part of the problem for carders, according to forum member “Telephone,” is the inherently limited geographic distribution of proxies in SOCKS, the obfuscation-friendly internet protocol used by Tor and all of the antidetect browsers known to Gemini. The SOCKS protocol works by facilitating the exchange of network packets from clients and servers via a proxy, enabling it to bypass network firewalls and connect to unauthorized websites.
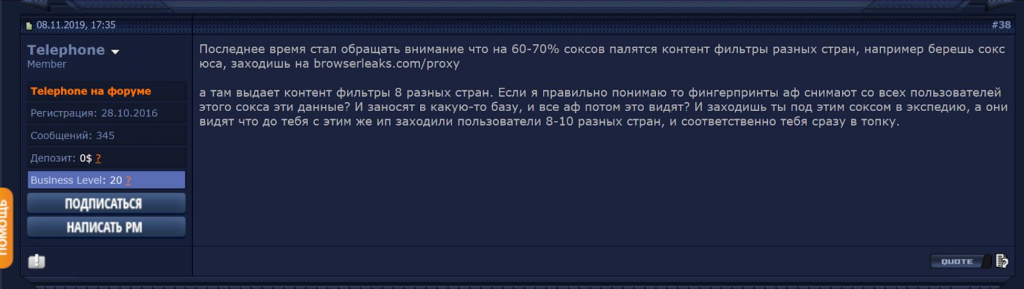

Image 9: Forum user Telephone explains why SOCKS offers little help in a November 8, 2019 Russian-language post.
Last November, Telephone posted the following on a top-tier Russian-language forum, regarding Expedia’s strong anti-fraud controls:
“Recently, I began to notice that 60-70% of Socks are being burned by content filters from different countries, for example, you take socks from the USA , go to browserleaks[.]com/proxy and there it gives out content filters of 8 different countries. If I understand correctly fingerprints are pulled from all users of this proxy? And they bring it into some kind of base, and everyone can see it? And you enter Expedia using this proxy and they see that users from 8-10 different countries entered using the same IP before you, and immediately you are burned.”
One technique that is taking professional carders to the next level, however, is virtual network computing (VNC), according to a February 2019 post from dark web forum member “benumb.” VNC is a type of remote-control software that enables cybercriminals to take control of a target’s computer over a network connection.
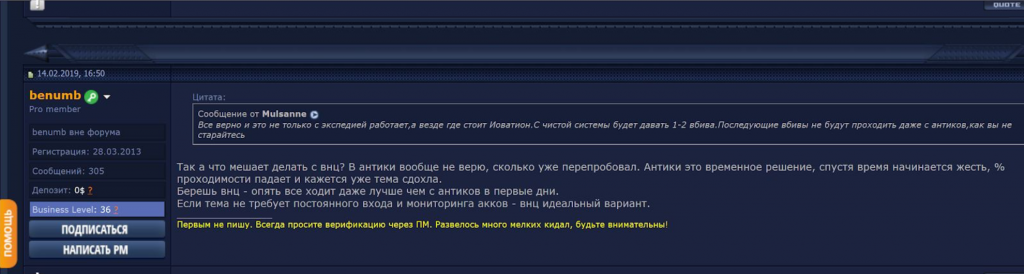

Image 10: In a February 14, 2019 post, forum member benumb explains in Russian why VNC is critical to carding OPSEC.
In the post above, benumb claims that remote control of a target’s device by way of VNC enables carders to bypass Iovation’s anti-fraud filters, illustrating the specificity of hardware fingerprints needed to successfully “do the scheme.”
Additionally, carders themselves do not have to be all that technically proficient to launch a VNC attack on a victim’s device. With the advent of the “crime-as-a-service” economy in the dark web, carders can purchase a dump of VNCs obtained via brute-forcing attacks for as little as $20. Below, a recent post from forum member “HugoBo$$” highlights the VNC market.
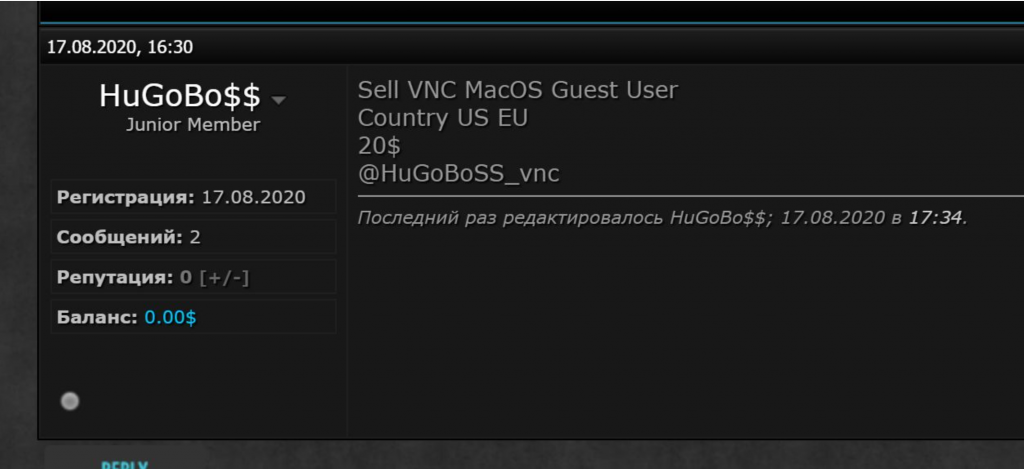

Image 11: HuGoBo$$ has VNCs from the US and EU for a low price.
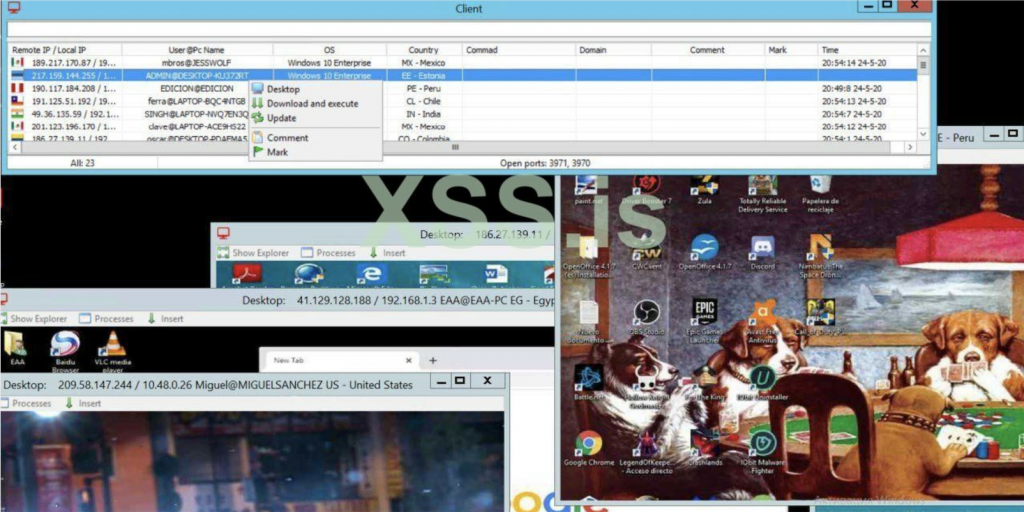

Image 12: Screenshot of a bundled VNC interface from an attacker’s device.
Both carding and anti-fraud technology have evolved greatly from the days of the “Carderplant” and in fraud forums that dominated the cyber-underworld in the first decade of the millennium.
As the enterprise enters a new decade marked by an unprecedented transformation in the realms of data, cloud computing, e-commerce, and instant payments, regtech – despite all of its advances – is still playing catch-up with cybercrime’s apex predators. Gemini research illustrates that, irrespective of the robust data-scraping and analytics mechanisms hardwired into anti-fraud systems, more skilled carders are still finding ways to take scores.
Facing tens of billions of dollars of CNP-related fraud losses over the next three years, merchants need to improve their defenses. Despite enhanced friction on the user-end, enterprises need to implement two-factor authentication within their payment gateways. Additionally, deeper fingerprinting at the hardware level and biometric data collection from end-users may further secure payments from fraud. But then again, hackers may eventually find a way to exfiltrate those fingerprints as well.
One of the barriers preventing many retailers from adopting more secure anti-fraud measures is their aversion to the price. However, the cybercriminal shift from Card Present (CP) fraud to CNP fraud, which began as e-commerce sites became more common and EMV chip technology undermined the viability of cloning CP cards, has recently accelerated. Lockdown measures related to the COVID-19 pandemic drastically reduced in-person transactions across much of the world, and as payments moved online, cybercriminals followed. Thus, the opportunity cost of not adopting anti-fraud measures is rising parallel to criminal demand for stolen CNP cards. Fraudsters opportunistically choose the path of least resistance, which sets retailers with poor e-commerce security squarely in their sights. In the wake of the pandemic, retailers of all sizes need to mitigate fraud losses and preserve all of the revenue they can. To this end, awareness of CNP fraud and all of its related cyber infrastructures has become vital business intelligence in the time of COVID.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate assets targeted by fraudsters and online criminals in real-time.