

As cybercrime levels around the world continue to rise, Australia has seen an increasing number of incidents. According to the Australian Institute of Criminology, there was $42 million USD in fraud in 2018, accompanied by an 86% increase in internal fraud investigations. Dating further back to 2016 and 2017, fraud was confirmed in 75% of all cases investigated, totaling $94 million USD lost.
The Australian Payments Network is a self-regulatory body designed by the payments industry in order to measure instances of fraud and improve the reliability of payment systems. While cyberfraud is on the rise in Australia and across the world, the rate of increase appears to be slowing in Australia, offering an optimistic outlook for the nation’s countermeasures. Extensive data from 2017 showed that the value of fraudulent transactions overall increased by 5% from the previous year, compared to a 16% increase in 2016 and a 19% increase in 2015. This diminishing rate of growth is a positive indicator for Australia’s mitigation efforts, particularly in comparison with regional neighbors.
The growth of online card fraud runs parallel with declining levels of skimming, a technique in which fraudsters use physical devices implanted at ATMs or point-of-sale (POS) terminals to capture card information. In 2017, skimming fraud fell to its lowest levels since 2006. This appears to be because of EMV chip implementation. In 2014, Australia mandated that all payment terminals be EMV chip compatible. This greatly increases the security of Card Present (CP) transactions and drastically lowers the success rate of card skimming. Accordingly, skimming losses fell 47.8% in 2017 to $30.9 million. Gemini data indicated that CP fraud exposure nonetheless increased during this time, which aligns with certain other advanced economies adopting EMV chips without a commensurate decrease in CP fraud (such as the United States and South Korea).
As CP fraud climbed, Card Not Present (CNP) fraud has remained relatively stable. A full 85% of all Australian fraud is now online, up from 78% in 2016. It represents a large sum of money; the Australian Payments Network reported that there was $767 billion USD worth of Australian card transactions in the 12 months from July 2017 to June 2018, with $565 million USD in fraud. One attack vector that has become far more popular among cybercriminal communities is formjacking, particularly through Magecart attacks. This involves injecting malicious JavaScript into a website after making an initial breach and is often used to steal sensitive customer information from e-commerce sites.
Gemini data has indicated that from July 2017 to June 2018, cybercriminals spent $6.3 million USD purchasing compromised Australian payment cards. Using the Australian Payments Network number, that would place the average return on investment (ROI) at $90 USD for each dollar spent. Since cybercriminals spent over $15 million USD on Australian payment cards in the past year, if the 9,000% ROI persists, this would yield approximately $1.35 billion USD in illicit gains.
Liability mostly falls on financial institutions rather than the customer. The Australian Payments Network Limited states: “Australian consumers are not liable for fraud losses and will be refunded as long as they have taken due care with their confidential data.” This is the default under the zero liability bargain, which, for practical purposes, insulates the consumer from any liability and pushes the cost to merchants.
While the Australian Payments Network Limited measures payment card fraud by the value of fraudulent transactions, Gemini calculated fraud rates by the quantity of compromised Australian-issued payment cards offered for sale in the dark web. During the past 12 months, approximately 974,000 CNP and 94,000 CP records were compromised. The CNP records contained a large amount of personally identifiable information (PII): 32% included cardholders’ phone numbers, 19% included email addresses, 1.2% included date of birth (DOB), and 0.08% included tax file numbers (TFNs; rough equivalent of US Social Security numbers). Of the CP records, only 72% were compromised within Australia. The second and third countries in which Australian-issued cards were compromised most frequently were the United States (18%) and the United Kingdom (2.2%), respectively.
In the 12-month period before this, from 2017 to 2018, there were 1,025,000 CNP and 63,000 CP records offered for sale in the dark web. These numbers demonstrate an unusual trend; CNP fraud decreased by 4.58% but CP fraud increased by 50.33%. Many countries across the world see the reverse as mitigating efforts against CP fraud drive cybercriminals to increasingly turn to CNP fraud. It should be noted that CNP fraud still comprises the majority of Australian cyberfraud by an order of magnitude.

Amidst these high fraud rates, Magecart attacks remain one of the most effective. This refers to injecting malicious JavaScript into a website after breaching it through employing brute-forcing attacks, phishing schemes, or social engineering. The breached website is then connected to a skimmer loader domain that delivers the skimmer’s JavaScript to infect the target system, from where the hackers collect sensitive customer information. In August and September, Gemini discovered over 100 malicious domains worldwide that employ Magecart skimmers, many of which are disguised as legitimate websites. Among the list of merchants targeted by this activity, Gemini identified that those with the domain extensions of [.]com, [.]uk, and [.]au were the most targeted. In conjunction with rising Magecart and fraud attacks, this indicates a likelihood that Australia will be among the most targeted countries.
The median price of Australian CNP cards during this time was $17 USD, while the median CP price was $45 USD. This marks an increase in both categories; during the previous 12-month period, CNP cards were $12 USD while CP cards were $21 USD. A price increase on this scale generally denotes either a reduced supply or increased cash-out reliability. The dark web median prices are $12.01 USD for CNP cards and for $16.80 USD for CP cards, both lower than the prices for Australian-issued cards.
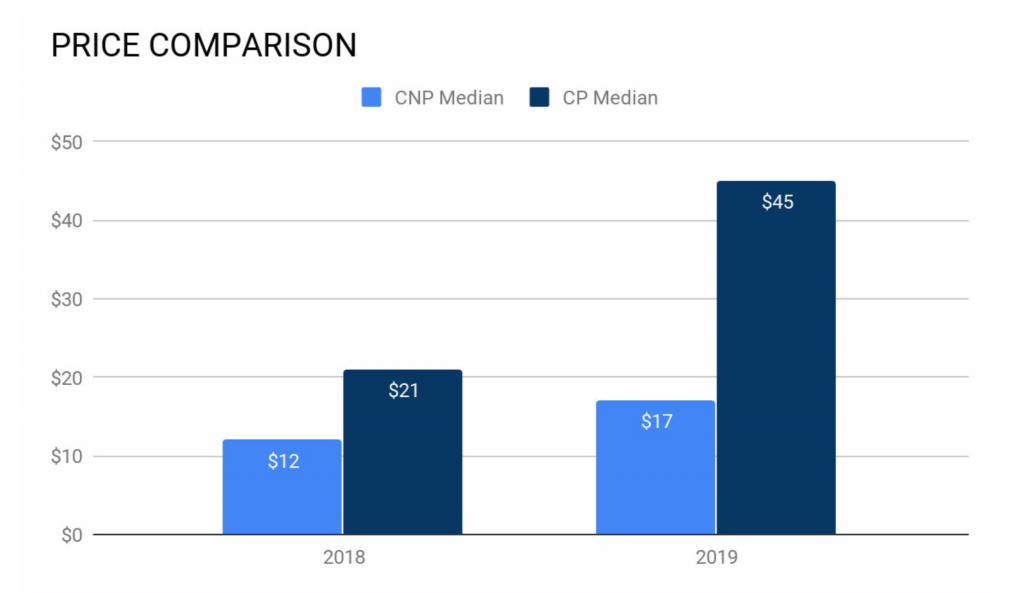

Image 2: Median prices of Australian-issued CP and CNP records display a large increase from 2018 to 2019.
Gemini collected data on the top five economies in the Asia Pacific (APAC) region to determine how many CNP and CP records were posted for sale in the dark web pertaining to each country (October 1, 2018 – September 30, 2019). The percent change from the previous year is marked next to the values.
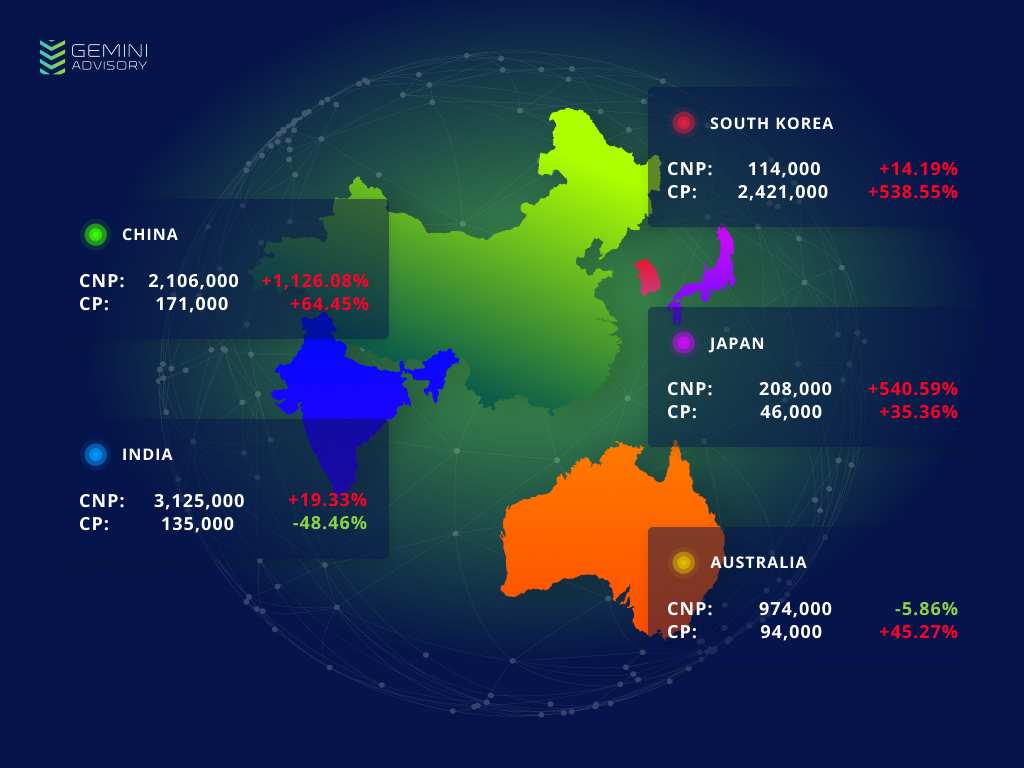

Australia was the only country of the top five APAC economies that saw overall fraud levels decrease during this period. Australia’s CNP payment card fraud dropped by 4.58%, which was greater than its 50.33% increase in CP fraud and resulted in an overall 1.39% drop in Australian payment card fraud. While India did have a drop in CP fraud by a full 48.95%, this was far offset by its 20.55% increase in CNP fraud, resulting in a 14.22% overall increase in exposure. Australia thus stands alone among APAC’s top five economies as the only country with a decrease in the volume of payment cards offered for sale in the dark web from October 1, 2018 to September 30, 2019.
It should be noted that the natural fluctuation of records added to the dark web may account for slight changes in overall card volume, so small, short-term trends either upwards or downwards are not necessarily indicative of larger trends or landscape shifts. The volume added may also shift due to single large breaches, such as in South Korea. Massive spikes in July, August, and September 2019 increased the overall yearly card volume of South Korean-issued records by a large margin, yet may simply represent anomalously large breaches and not a shift in the value or demand for South Korean cards.
One of the most notable cybercrime incidents in recent months was a breach of the Australian National University. This compromise exposed the PII of 200,000 individuals from records dating back 19 years. Among the exposed PII were names, addresses, DOBs, phone numbers, personal email addresses, emergency contact details, TFNs, payroll information, bank account details, passport details, and student academic records. The culprit has yet to be found, but allegations of Chinese-linked Advanced Persistent Threat (APT) activity have circulated among security researchers and government agencies. Beijing denies the allegation.
While this single incident represents a massive exposure of sensitive PII, if the APT allegations are true, most of the victims are unlikely to undergo financial harm because of this breach. Another rising attack vector, by contrast, has more dire implications for cardholders’ financial security. KPMG global fraud lead and KPMG Australia Partner Natalie Faulkner detailed the increasing prevalence of social engineering schemes designed to obtain payment card information. “We are seeing a disproportionately high volume of scam attempts on Australians – there were 177,000 scam reports here last year, costing almost half a billion dollars. This compared to around 85,000 scam reports in the US and UK, with far bigger populations. This covers a wide variety of scams – defined in our report as ‘social engineering’ frauds – including investment, romance, crypto-currency, false billing and tax office/government agency scams.”
Gemini can corroborate these claims, having observed massive amounts of records offered for sale across the dark web with high levels of PII, often including payment card data, Social Security numbers (SSNs), DOBs, passport details, email addresses, phone numbers, and user-agent information. Analysts discovered up to 1.6 million such records globally in the dark web in the past year. Phishing attacks that grant threat actors access to victims’ PII enable them to enact complex and intrusive fraud schemes, such as directly accessing victim bank accounts, tax refund fraud, and the creation of synthetic identities.
Since social engineering attacks do not require fraudsters to directly breach payment systems or hack sophisticated software, it must be combated through improving best practices. As the points of entry are the targets themselves and the attacks rely on deception, individuals must become better informed about common scams and stay vigilant about illicit attempts to obtain their financial details.
Cybercrime may affect nearly every industry, but it does not affect them all equally. The Office of the Australian Information Commissioner (OAIC) published a comprehensive report on data breaches from Q1 2019, which detailed the most prevalent attack vectors. A full 67% of cybercriminal breaches involved compromised or stolen credentials (40% unknown method, 20% phishing, 7% brute-forcing).
The most affected industries were Health Service Providers (58 notifications), Finances (27 notifications), Legal/Accounting/Management Services (23 notifications), Education (19 notifications), and Retail (11 notifications). Health Service Providers make particularly alluring targets worldwide because they often contain sensitive medical, insurance, payment, and personal information, and also tend to lack the sophisticated cybersecurity apparatuses of many large financial institutions.
Australian laws mandating adherence to cybersecurity standards are aimed at reducing fraud rates nationwide. Part IIIC of the Privacy Act, for example, outlines requirements for the country’s Notifiable Data Breach (NDB) Scheme, a system that requires entities to register breaches “likely to cause serious harm” in a national database. Consolidated databases such as this one provide organizations with the statistics needed to design data-driven mitigation strategies.
The Australian Payments Network has also adopted several steps to reduce cybercrime rates. With 130 members and participants from financial institutions, retailers, and payment system operators, the network’s regulations provide impactful fraud countermeasures for the industry. For example, merchants with a fraud rate above a benchmark fraud risk level are required to employ multi-factor authentication for transactions, providing a second layer of security. It invokes new global standards in calling for payment tokenization, 3D Secure protocol, and Secure Remote Commerce, all of which are methods to secure CNP transaction data and add extra cardholder authentication.
As debate increasingly shifts towards passing some financial liability to banks for fraud incidents currently covered by merchants, some financial institutions are taking proactive steps to reduce fraud. The National Australia Bank (NAB) is using what it terms “preferential” pricing to enable small businesses to use discounted cybersecurity tools, including Cisco’s cloud-based Umbrella product. This demonstrates the initiative Australian banks are taking to influence security practices at large and small-scale firms.
The Australian government has acknowledged that cybercrime is an international threat that requires multilateral security measures, and has accordingly taken steps to combat cybercrime in the Indo-Pacific region. Its International Cyber Engagement Strategy aims to increase cybercrime awareness in this region, assist neighboring countries in strengthening their cybercrime legislation, improve law enforcement and prosecution capacity, and encourage international information sharing. This initiative seeks to directly address safe havens, or countries from which cybercriminals can launch attacks against international systems with little threat of domestic prosecution or extradition.
The Australian Federal Police have launched Cyber Safety Pasifika (CSP), a cybercrime education program supporting Pacific Island nations. In this spirit, Australia has assisted Tonga to strengthen its legislative capacity so that it became the first Pacific Island country to adhere to the Budapest Convention’s international cybercrime cooperation standards. Australia has launched similar initiatives as well as intelligence-sharing networks with other APAC countries. It also cooperates through the Five Eyes intelligence alliance, United Nations Office on Drugs and Crime (UNODC), the Council of Europe, EUROPOL, and INTERPOL.
Australia’s cybercrime rates and volumes of compromised payment card information paint a rare optimistic image. While most nations around the world see dramatic increases in payment card fraud, Australia has kept this relatively level. Official statistics indicate declining rates of fraud growth, while Gemini’s dark web monitoring indicates an overall decrease in compromised payment cards added to the dark web. The increase in the median dark web price of Australian-issued CNP cards aligns with the reduced supply, while the CP price increase may indicate increased cash-out reliability.
Australian laws and initiatives designed to mitigate the negative effects of cybercrime and fraud have shown decisive and concrete action. The NDB Scheme and Australian Payments Network standards have raised the level of domestic security compliance, while the International Cyber Engagement Strategy reaches beyond the country’s borders to build anti-fraud capabilities regionwide. In the perpetual arms race between cybercriminals and security officials, Australia appears to be keeping pace. Gemini Advisory assesses with a moderate degree of confidence that Australia will likely remain a regional leader in cybersecurity policy and is likely to see a relatively stable level of cyberfraud in the near future.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate assets targeted by fraudsters and online criminals in real-time.