
By Stas Alforov
In 2015, the US financial industry began a massive migration to the EMV standard in response to overwhelming levels of payment card fraud.The inherent security of EMV technology in chip-enabled cards provides end-to-end encryption during card-present transactions, and effectively prevents payment card counterfeiting. EMV rollout was poised to disturb the market for compromised credit and debit cards and significantly reduce fraud losses to US-based banks and retailers.
As we have passed the three-year anniversary of the US EMV migration deadline, it is evident that the majority of financial institutions were successful in providing their customers with new EMV enabled cards. However, contrary to the prevailing logic, migration to the EMV did not eradicate the card-present fraud. Of more than 60 million payment cards stolen in the past 12 months, chip-enabled cards represented a staggering 93%.These results directly reflect the lack of US merchant compliance with the EMV implementation.
Based on the proprietary Gemini Advisory telemetry data collected from various dark-web sources over several years, we have determined that in the past 12 months at least 60 million US cards were compromised. Of those, 75% or 45.8 million were CP records, likely compromised through card-sniffing and point-of-sale (POS) breaches of businesses such as Saks, Lord & Taylor, Jason’s Deli, Cheddar’s Scratch Kitchen, Forever 21, and Whole Foods. To break it down even further, 90% or 41.6 million of those records were EMV chip-enabled.
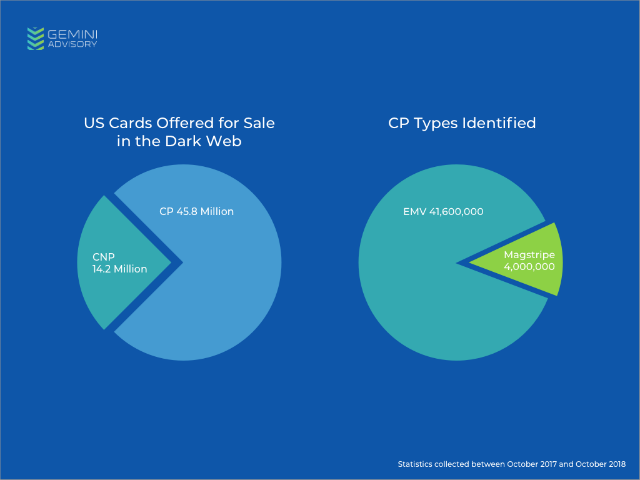

Image 1: The number of stolen chip-enabled EMV vs. magnetic payment cards in the US
Furthermore, the shift in Card-Not-Present (CNP) fraud is becoming more evident with a 14% increase in payment cards compromised through e-commerce breaches in the past 12 months. Payment card data that that was stolen from Orbitz, Ticketmaster, City of Goodyear, and British Airways represented only a small part of the 14.2 million CNP records posted for sale in the past 12 months.
In the past 12 months ~15.9 million compromised Non-US payment cards were posted for sale in various dark-web sources, split between 11.3 million CNP records and 4.6 million CP records, of which 4.3 million CP records were EMV enabled. This demonstrates that the theft level of EMV-enabled card data in the US is 868% higher or a difference of 37.3 million records compared with the rest of the world combined.
It is thus clear to say that US is the most targeted country when it comes to credit card fraud, but it is also evident that EMV implementation has successfully made its impact in most countries outside of the US.
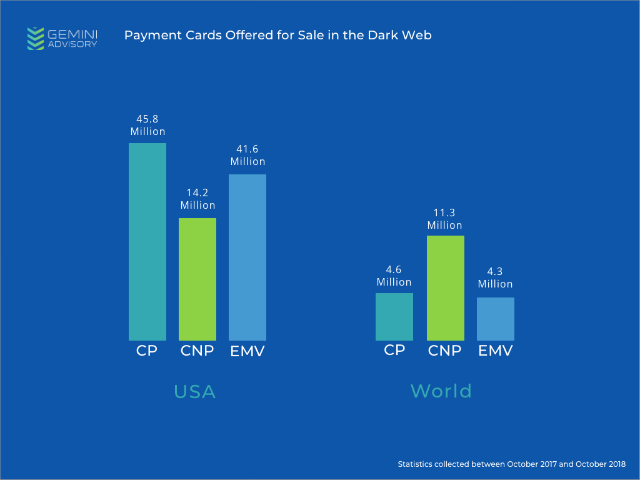

Image 2: The comparison between stolen payment cards in the US and worldwide.
Financially motivated threat group 6 (Fin6) and 7 (Fin7) are notorious for compromising the merchant networks, finding their way to POS terminals on the targets network, and deploying POS malware. In the case of previous Fin6 attacks, the group infected POS terminals with the malware known as TRINITY or FrameworkPOS. According to FireEye researchers, TRINITY runs continuously and targets system processes not listed in its accompanying process blacklist, seeking data that matches payment card track data. Once the malware identifies track data, it is copied, encoded and then finally exfiltrated to a command and control server (C2).
Card-present data is also collected via a more manual method by so called skimmer groups, who are utilizing custom made hardware known as “shimmers” to record and exfiltrate data from ATMs, and POS systems. Shimmers sit between the chip on the card and the chip reader in the ATM or point-of-sale device, recording the data on the chip as it is read by the underlying machine. Shimmers are only successful in recording track 1 and track 2 data when the payment card’s issuing bank neglects to check the dynamic CVV during the transaction. If the EMV functionalities are not fully deployed, the track 1 and track 2 data stolen from the chip transaction can be easily encoded by the fraudster onto any magnetic strip. Once the payment card data is stolen by either of the two methods mentioned above, it is often placed for sale on various dark web criminal marketplaces where it is then accessible 24/7 to other cyber criminals.
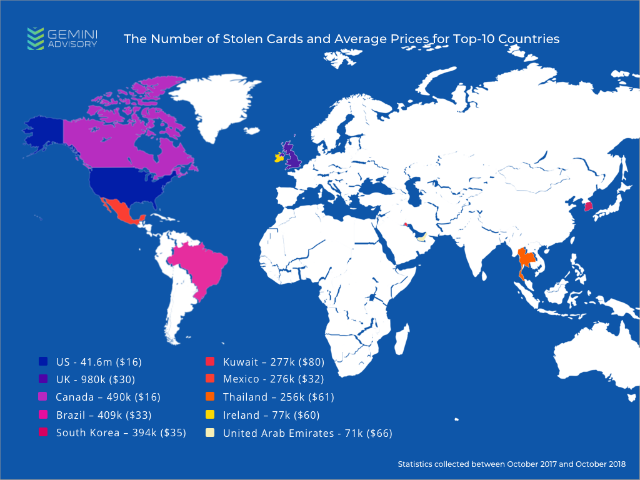

Image 3: The average prices of stolen credit cards in Top-10 countries.
The majority of card holders have been issued EMV enabled chip cards with a built-in fall back magnetic stripe which allows the cards to still be swiped at POS terminals. The swipe feature allows the card holders to utilize their cards at merchant locations that have not fully transitioned to EMV enabled POS systems, and also allows the card holder to fall back to the swipe method if the EMV chip is malfunctioning or damaged. Currently, refueling stations are the only merchant that is not liable for the EMV shift until October 2020, meaning that they have the choice to continue to provide a swipe only option for the next two years without taking any liability or fault for any fraud that might occur at their locations, which could have been prevented via EMV.
As 2018 comes to a close, besides refuelling stations, there are numerous merchant locations that are still asking their customers to swipe rather than use the chip insert method, thus completely neglecting the EMV security features. This often happens because the merchant does not have an upgraded EMV enabled POS or the merchant has the EMV enabled POS system but is not using its full capabilities. In some cases, retailers are opposing migration to newer EMV technology because of the inherent high cost of the equipment.
To fully upgrade the hardware and software of a POS terminal, the price tag could be upward of several thousand dollars which is often a pricy burden for small to medium size businesses, leaving them exposed to CP fraud.
With most large US merchants fully transitioned to EMV, the attention turns to gas pump terminals and small/medium size businesses as the victims of opportunity. In addition, in response to widespread hacking incidents, large and enterprise-level companies have made significant investments in information security, training of personnel and infrastructure defence. However, smaller businesses are only now beginning to understand the importance of such programs, and are thus providing a sufficient budget allocation toward them. Because Gemini Advisory believes that criminal groups will always sway to the path of least resistance, we predict that financially motivated threat groups such as Fin6 and Fin7 will be more likely to turn their resources onto small to medium sized businesses with 10-50 locations. Since such businesses are less likely to have fully implemented the EMV transition, criminals would be able to rely on their current TTPS for card data exfiltration.
Until EMV implementation is more widespread amongst US merchants, Gemini Advisory recommends the usage of mobile payment systems like Android Pay, Google Pay, and Apple Pay. Such payment systems are not susceptible to shimming devices or POS malware, making them the most secure payment method currently available.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate the ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate in real-time assets targeted by fraudsters and online criminals.