

In October 2020, Gemini analysts observed a criminal actor advertise in the dark web a new tool called “Email Appender” that implants emails directly into a target mailbox. This allows attackers to put malware-infected or tailored phishing emails into victims’ mailboxes without actually sending the email, thereby bypassing email security platforms that inspect messages en route to their destination mail server. This new tool poses a significant risk to both individuals and businesses as it raises the success rate of malware attacks, allows for more sophisticated phishing and business email compromise (BEC) campaigns, and opens the door for simplistic ransomware-like attacks. It is also important to note that while the software provides a simple way for hackers to implant emails, the underlying methodology can be achieved through multiple other routes.
While Email Appender is geared toward more sophisticated phishing and malware distribution, the actor behind the software previously released a simpler email spam service called “GetMailer Pro” in early 2019, which Gemini has reposted here. The software claims to emulate the email clients of Yahoo, AOL, mail.com, and others for the purpose of automated mass email creation and delivery. Unlike Email Appender, emails sent through GetMailer Pro do not evade anti-spam and anti-fraud filters used by recipients’ email platforms. The older service does, however, employ a similar user interface to Email Appender and is offered through the same subscription pricing model, albeit at half the price.
Attackers using Email Appender must first acquire a list of valid credentials in the form of email addresses and associated passwords. Listings containing this information are widely available in the dark web at little or no cost. While the acquired credentials might not be specifically associated with the email account, the prevalence of shared passwords across accounts leads to a reasonably high possibility of authentication to the mail server.
Once the attacker has uploaded the compromised email login credentials into Email Appender, the software checks for valid credentials and connects to the email accounts through Internet Message Access Protocol (IMAP), the standard protocol email clients use to receive messages from a mail server. A unique feature of the IMAP protocol allows a properly authenticated user to append a message to their mailbox. An attacker, using this feature, can thus “implant” emails directly into the victim’s mailbox as opposed to sending them through traditional channels. This is critical because it means that the emails bypass the email platform’s security tools that validate IP addresses and scan for modifications or malware while the email is in transit between the sender and recipient.
Furthermore, email platforms typically monitor the IP addresses of users attempting to connect to an account via IMAP to prevent unauthorized or unusual activity. To overcome this security precaution, Email Appender can be configured to use SOCK proxies, which allow attackers to set their IP address to a location that they believe will deceive email platform security. To make matters worse, Email Appender also comes pre-packaged with 10,000 IMAP server configurations that can be updated as needed, and the software can analyze victims’ email addresses to identify which server connection should be used.
Once the attackers have connected to the email accounts via IMAP, they can customize the email messages to their criminal purposes and then implant the messages in bulk to compromised accounts. For example, attackers can set the Sender field to an email address that will enhance the perceived legitimacy of the message. Since the message is not actually being routed through the internet, the Sender field can be set to the actual email address of the company or person being impersonated. This stands in contrast to typical email schemes that are forced to slightly alter the spelling of the actual email address.
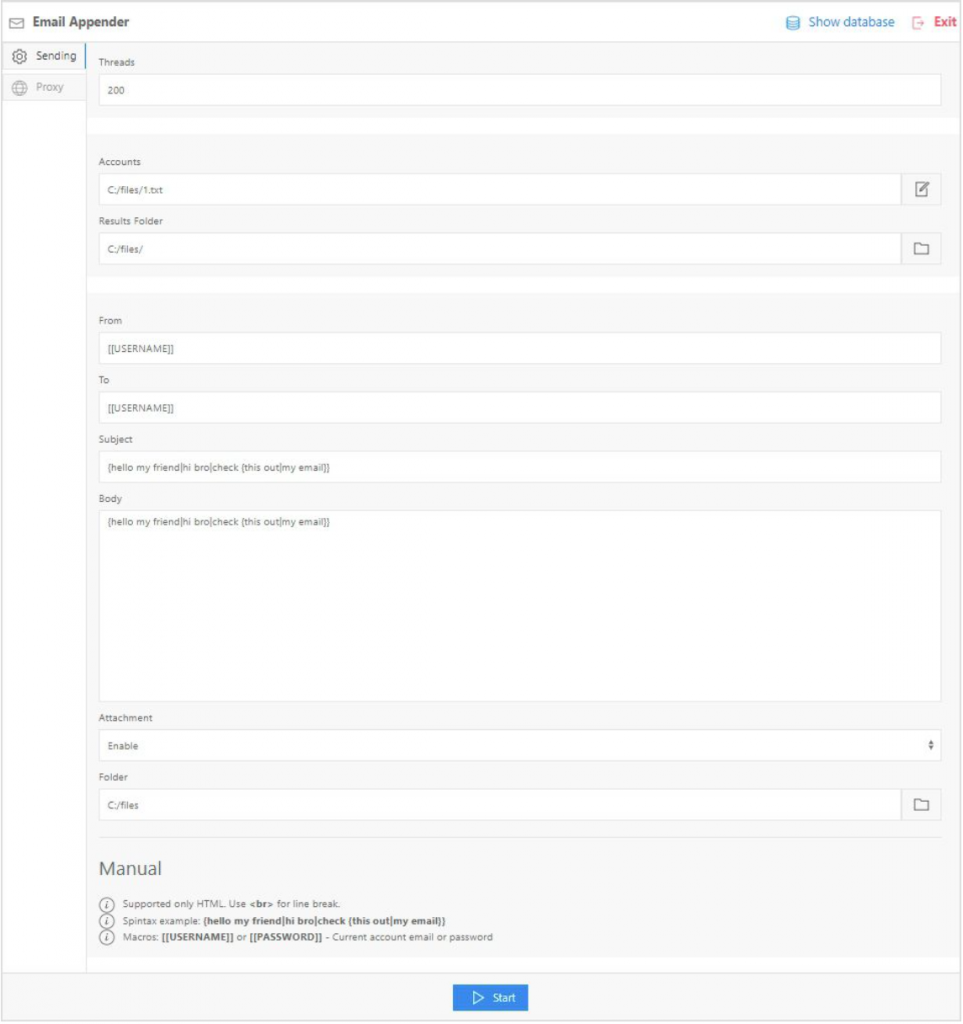

The modified Sender field can then be combined with changes to the From field and Reply-To field to increase the attackers’ success rate. The From field designates the display name shown next to the email address (e.g., Legitimate Business Support<[email protected]>), and many mail clients only present the first portion (e.g., Legitimate Business Support) in their message listing. By modifying these fields, the attackers can boost the perceived credibility of the message. The Reply-To field designates where reply emails are sent to, allowing attackers to redirect responses to an email address under their control and away from the falsified Sender and From addresses. In effect, this enables attackers to social engineer targets through email correspondence and prevent replies to the legitimate person or company.
Using these tools together, attackers could implant an email message that appears to be sent from [email protected], with the display name Legitimate Business and the Reply-to field set to [email protected]. Depending on the attacker’s intent, the body of the email could contain a link to a site that will steal sensitive information or include a malware-infected attachment. For the average user, this email would appear more legitimate than standard phishing emails.
Technical Aspects
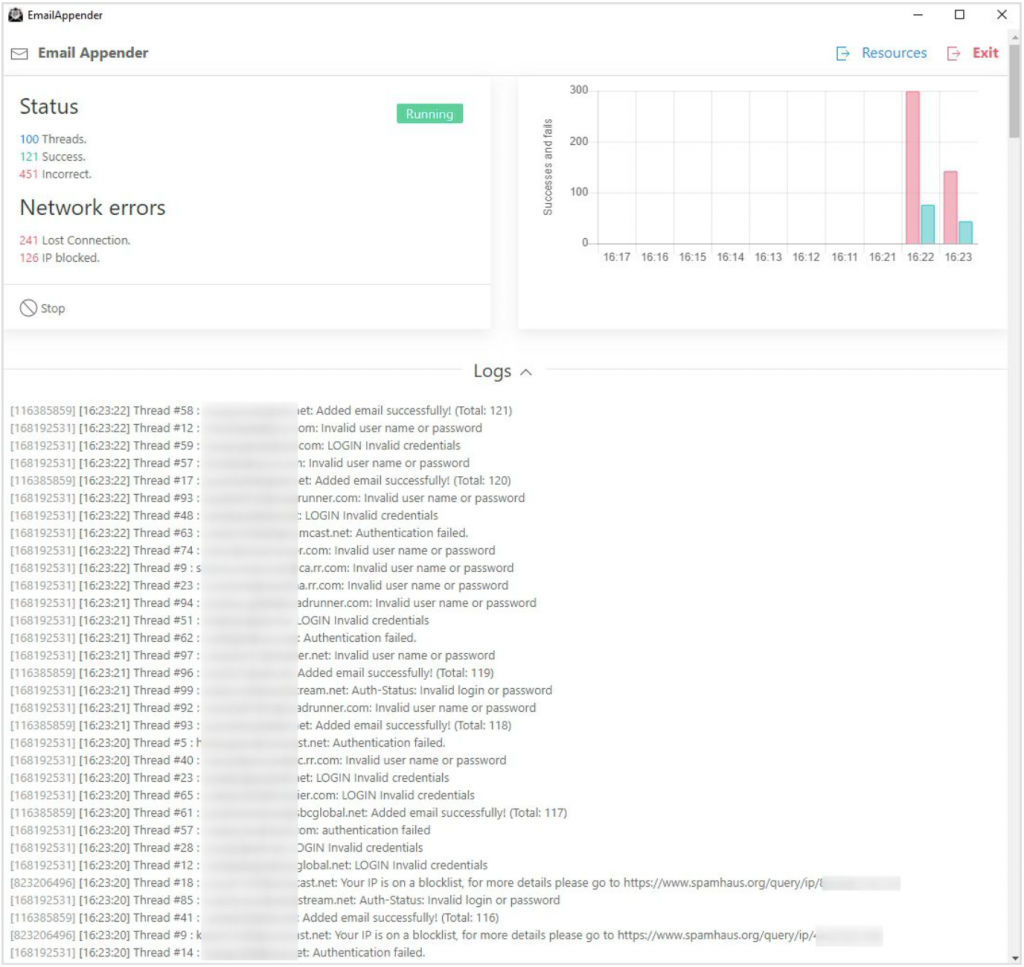
From a technical point of view, the criminal actor behind Email Appender noted that the software is written in Node JS, compiled into an MS-Windows executable, and requires a system with at least four CPU cores, four gigabytes of memory, and a solid-state disk drive for optimal performance. The software uses a multithreaded approach to implanting the messages to increase performance, and the interface provides a monitoring view that shows current utilization statistics and logging for the batch being processed.
The criminal actor behind the software is offering Email Appender to hackers in the dark web as a subscription and posted a brief walkthrough on YouTube, which Gemini has reposted here. The technique exploits compromised credentials to implant an email via IMAP, and the software provides a simple interface and amplifies the technique by targeting all mailboxes in a vulnerable account listing.

Through phishing, cybercriminals often attempt to obtain sensitive information from victims by pretending to be trustworthy entities, such as reputable companies or acquaintances of the victim. In the context of email, phishing relies on the victim believing that the malicious email is in fact legitimate. Traditionally, to raise the chances of success, attackers use email addresses that appear very similar to legitimate ones and mask messages with the text and visuals used by the legitimate company or individual. However, as the general level of cyber awareness has risen in recent years, a segment of internet users previously vulnerable to phishing has begun validating suspicious email addresses against companies’ official addresses. This, along with better detection of spam near the point of delivery, has led to a decrease in the effectiveness of spamming. Unfortunately, Email Appender negates these positive trends by enabling attackers to exactly mimic the Sender and From fields of an impersonated company and bypass the spam detection systems.
Business email compromise (BEC) refers to a specific type of phishing that leverages compromised business emails to extract more valuable information than from a typical individual. With BEC, a criminal impersonates an employee within the company (such as a senior manager or IT administrator) or someone from a partner business (such as a supplier) and deceives the victim into divulging valuable information. Typically, for BEC to be most effective, the attacker would need access to the account of an influential employee or partner to extract valuable information from another employee. However, with Email Appender, the attacker could gain access to a relatively less important employee and then implant emails impersonating the more influential person.
In a similar manner to phishing, the success rate of email-distributed malware is largely a product of recipients’ trust in the legitimacy of the email. Email Appender not only increases the apparent legitimacy of emails as noted above, but also allows attackers to entirely sidestep the email platform security features designed to flag possible malware or suspicious senders. This, in effect, removes the two clearest indicators of a possible malware-infected email for most users: a flag from the email platform and a suspicious email address.
While Email Appender is not ransomware, the software does allow attackers to perform attacks similar in design. Ransomware generally encrypts a victim’s data and prompts the victim to send payment in order to regain access. With Email Appender, an attacker could make a copy of a mailbox and then delete the emails from the victim’s mailbox, resulting in a primitive imitation of ransomware. Should the victim fail to meet the attackers’ demands, the attacker could then publish the emails if they contained sensitive information.
The Email Appender software provides a novel means to conduct campaigns in support of malware infection and phishing, one that could prove difficult to detect and prevent for some email implementations. The easiest security enhancement for the individual account would be the use of multi-factor authentication (MFA) since it prevents connections to the account via just username and password. Most of the major email providers (i.e. Gmail, Yahoo, Outlook) offer MFA capability, although it is not mandatory. Some of these providers also provide alerting when an account is accessed from a different device or IP address. While this does not prevent the use of this technique, it should alert the user to the compromise of their credentials and hopefully prompt them to change their password and enable MFA.
Furthermore, corporate and government mail configurations are not immune to being compromised by this technique; many offer IMAP connectivity alongside their Bring Your Own Device (BYOD) programs. The security of these configurations should also benefit from implementation of MFA, though other protections at the Network or Application level could also be used.
Email systems are an invaluable transport and storage mechanism for information exchange on the internet. For that reason, exploitation of email systems and their accounts will almost certainly maintain a top spot on the hacking community’s exploitation target list. In many ways, the earlier service offered by the actor, GetMailer Pro, matches the well-established interest among criminal actors for software that expedites the distribution of phishing and malware campaigns. Therefore, it is the second service, Email Appender, that signals the more worrying development: criminal actors have made their next move to outflank existing anti-spam and anti-fraud security precautions by moving to email implantation. The ball is now back in the cybersecurity practitioners’ court.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate assets targeted by fraudsters and online criminals in real-time.