
The greatest targets of cybercriminal activity have consistently been wealthy countries for the simple reason that there is more to steal. However, as internet penetration increases across the developing world and payment activity shifts online, developing nations have increasingly become targets themselves. Pakistan, for example, has historically seen low levels of cybercriminal targeting. However, recent Gemini Advisory analysis, alongside that of several other security organizations, indicates a significant escalation in compromised Pakistani payment records.
In recent months, several security organizations have reported on massive payment card fraud targeting Pakistani financial institutions. In light of the country’s history of limited targeting by cybercriminals, the scale of these compromised records is notably large.
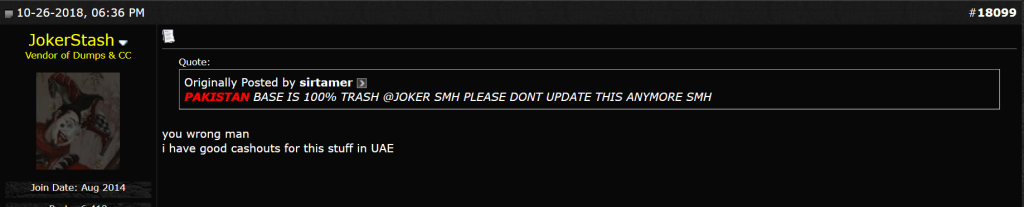
The Computer Emergency Readiness Team for Pakistan, PakCERT, released the PakCERT Threat Intelligence Report PCTI-2018-0111 on November 4, 2018, a report claiming that over 9,000 compromised debit cards (largely belonging to Pakistani bank customers) were posted to the dark web on October 26, 2018. The report asserts that while BankIslami was the most publicly recognized bank to be compromised in this breach, a number of other banks had compromised records posted to the dark web as well. This report appears to focus on the 2018 breach, which appears to consist of the first half of the cards posted to the dark web marketplace Joker’s Stash.
On February 22, 2019, threat intelligence company Group-IB reported on the compromised Pakistani cards posted to Joker’s Stash in January. The researchers claim that these records were posted in 2019 and include both the dump of records and the corresponding PINs. Group-IB reported that compromised credit and debit cards collectively worth $3.5 million USD were derived from Meezan Bank Ltd.
Pakistani banks have been slow to adopt EMV cards. According to propakistani[.]pk, the State Bank of Pakistan (SBP) issued a June 2019 deadline for EMV implementation across all banks, yet recently pushed back this date to the end of 2019 due to slow uptake. JS Bank notably became the first bank in Pakistan’s banking industry with an ATM network fully compliant with the more secure EMV standards on August 7, 2018.
Shortly after the initial breach was detected in October 2018, several banks took steps to mitigate damages. According to the PakCERT report, “several others bank [sic] issued security alerts and either completely blocked customer’s [sic] debit and credit cards or blocked their online and international use. Customers were sent SMS notifications of the changes.”
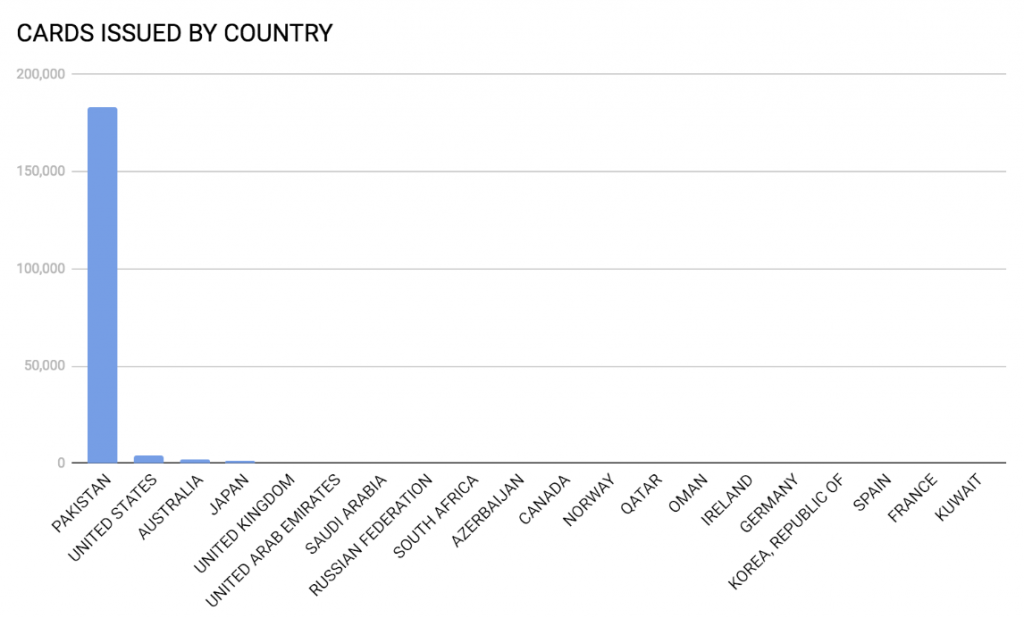
Gemini analysts have identified 260,000 Card Present (CP) payment cards with a total value of around $25 million USD associated with reported Pakistani payment card breaches that were posted for sale in a dark web shop, Joker’s Stash, between October 26, 2018 and February 25, 2019. Joker’s Stash is one of the oldest and most infamous dark web marketplaces. It has been associated with selling compromised data from major breaches, such as Bebe Stores, British Airways, Chipotle, Hilton Hotels, Jason’s Deli, Lord and Taylor, Saks Fifth Avenue, Sonic, and Whole Foods.
The data posted to Joker’s Stash was divided among five different bases. The original base, “PAKISTAN-WORLD-EU-MIX-01,” was posted on October 26, 2018, and totaled over 10,000 records with a median price of $100 USD. It included only Track 2 Data. The second and third bases, “PAKISTAN-WORLD-EU-MIX-02” and “PAKISTAN-WORLD-EU-MIX-03,” were respectively posted on October 31, 2018 and November 13, 2018, totaling over 190,000 payment records with a median price of $110 USD. They included both Track 1 Data and Track 2 Data. Through a deeper analysis of this data, it appears that the point of compromise was located in Pakistan and had affected non-Pakistani cardholders traveling from various other countries, likely indicating that this data was compromised in highly traveled tourist areas.

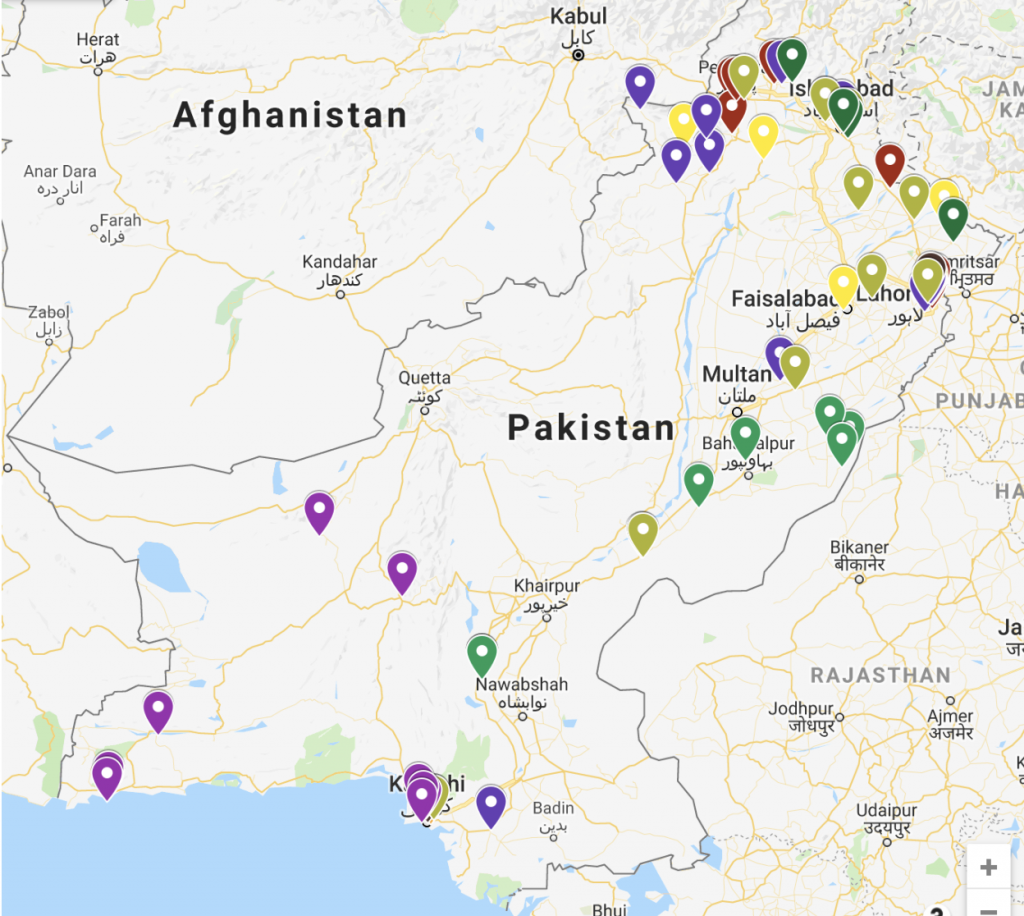
Gemini analysts located financial institutions affected by the records in the first three bases of this breach and determined that they largely came from Pakistan. While several threat actors complained about the difficulty with cashing out compromised payment cards outside of Pakistan, another threat actor specifically referenced the UAE as a viable country for cashing out these records, and several compromised financial institutions also have UAE locations.

The final two bases, “PAKISTAN-D+P-01” and “PAKISTAN-D+P-02,” were respectively posted on January 24 and January 30, 2019, totaling to roughly 57,000 payment records with a median price of $50 USD; they only included Track 2 Data and the records purportedly had PIN information. All of these records were associated with a single Pakistani financial institution: Meezan Bank Ltd. The significance of the total compromised cards from a single financial institution in these bases, and with the addition of stolen PIN data, indicates a potential breach in Meezan Bank’s banking system. If the threat actors had installed skimmers at Meezan Bank ATMs to intercept card data, they would have likely captured some records from other banks as well; since the records exclusively belonged to Meezan Bank, this further supports the likelihood of a Meezan Bank system breach.
In most cases, fraudsters can capture both the card and PIN data by employing card skimmers and cameras or overlays. However, fraudsters who use such techniques can often cash out the cards themselves, since they can use the stolen card data to clone the payment cards and use the PIN for ATM cash withdrawals. While this is the most common scenario, fraudsters appear to have identified a new way of acquiring card data with PIN information in large quantities in this breach, possibly by penetrating the banking systems themselves.
Gemini’s proprietary data, collected in the past several years across various dark web marketplaces specializing in the sale of stolen payment card data, indicates that nearly 13,000 Pakistani-issued cards were compromised prior to the recent breaches from October through February. The cards were primarily compromised in Pakistan and consisted of 91% Card Not Present (CNP) records and 9% CP records. The difference in compromised cards between the previous two years and the recent breaches between October 26, 2018 and February 25, 2019 consisted of around a 22,000% increase in compromised CP records in Pakistan. Such a dramatic increase in stolen data indicates that cybercriminals have identified a far easier or far more penetrating method to compromise cards in Pakistan. This has also led to a 100% increase in demand for Pakistani-issued CP cards since October of 2018.
Dark web reactions to the breach were mixed, with some threat actors purportedly having difficulty cashing out the compromised records. This is likely due to certain Pakistani banks blocking international transactions to mitigate damages from the breach. Other cybercriminals offered solutions to these problems, such as by cashing out the records in the UAE.


Gemini analysts assess with a moderate degree of confidence that the compromised Pakistani payment card data posted between October 26 and November 13, 2018 is associated with a merchant compromise in a major Pakistani city due to the inclusion of a notable number of foreign-issued compromised cards in the breach. In addition, Gemini analysts assess with moderate confidence that the second compromise that was posted between January 24 and January 30, 2019 is associated with a compromise of Meezan Bank Ltd’s internal systems. The crosshairs that appear to have been placed on Pakistan could potentially indicate a new trend in 2019: as more countries implement EMV, cybercriminals may target less wealthy countries with less developed banking infrastructure.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate assets targeted by fraudsters and online criminals in real-time.