
On March 28, 2018, a notorious hacking JokerStash syndicate, also known as Fin7 announced the latest breach of yet another major corporation, with more than five million stolen payment cards offered for sale on the dark web. Several large financial institutions have confirmed that all tested records had been used before at Saks Fifth Avenue, Saks Fifth Avenue OFF 5TH, a discounted offset brand of luxury Saks Fifth Avenue stores, as well as Lord & Taylor stores.
Although at this moment it is close to impossible to ascertain the exact window of compromise, the preliminary analysis suggests that criminals were siphoning the information between May 2017 to present. Based on the analysis of the available data, the entire network of Lord & Taylor and 83 Saks Fifth Avenue locations have been compromised. The majority of stolen credit cards were obtained from New York and New Jersey locations.
On March 28, 2018, notorious hacking JokerStash syndicate infamous for its long streak of successful high-profile breaches, including Whole Foods, Chipotle, Omni Hotels & Resorts, Trump Hotels and many more, has announced the release of the newest batch of compromised records called BIGBADABOOM-2.


With the declared number of compromised payment cards being in excess of five million, the current hacking attack is amongst the biggest and most damaging to ever hit retail companies.
Using our analytical tools, which were specifically developed in order to empower financial companies to monitor assets portfolio exposure within the deep & dark web, we have established with a high level of confidence that victims of the attack are Saks Fifth Avenue, Saks Fifth Avenue OFF 5TH, a discounted outlet of the luxury department store Saks Fifth Avenue, and Lord & Taylor Stores. Both companies are operated by Canadian retail business group Hudson’s Bay Company (HBC). Despite the fact that HBC owns other retail brands, namely Galeria Kaufhof, and Home Outfitters, it appears that only Saks Fifth Avenue and Lord & Taylor were affected in this breach. The company also operates Gilt.com, a popular online shopping website.
As of this writing, only a minor part of compromised records have been offered for sale, with approximately 35,000 records for Saks Fifth Avenue and 90,000 records for Lord & Taylor.
Considering the rather standard practice of marketplace operators in releasing stolen data gradually in order to avoid oversaturation of the market and to minimize the chances of identification of stolen records by the banks, it will take at least several months before the entire archive is offered for sale. For example, in the previous breach of Jason’s Deli Restaurants in December of 2017, the JokerStash syndicate has announced that they stole five million payment cards; however, up until now, only approximately a quarter of all payment cards were released for sale.
Despite the fact that the number of stolen records in both breaches is identical, the potential damage to cardholders could be significantly higher in the latest hacking attack. While diners at the affordable fast-food chain are less likely to purchase hi-end electronics like Apple computers and Microsoft Surface Books, which are coveted by cybercriminals for their high liquidity, it is also easier for banks to identify unusual shopping patterns and promptly block out-of-pattern transactions. However, cardholders who frequently shop at luxury retail chains like Saks Fifth Avenue are more likely to purchase high-ticket items regularly; therefore, it will be extremely difficult to distinguish fraudulent transactions from those of a legitimate nature, allowing criminals to abuse stolen payment cards and remain undetected for a longer period of time.
Based on the analysis of records that are currently available, it appears that all Lord & Taylor and 83 US based Saks Fifth Avenue locations have been compromised. In addition, we identified three potentially compromised stores located in Ontario, Canada. However, the majority of stolen credit cards were obtained from New York and New Jersey locations.
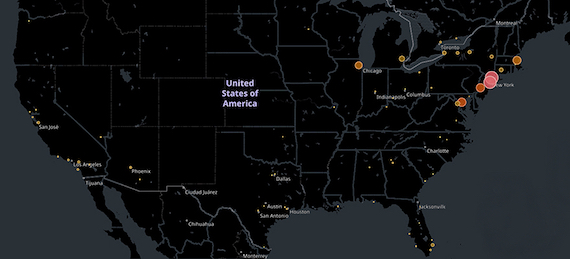

Estimated Window of Compromise: May 2017 - Present
Exposed US Locations: 83
Top-5 Exposed Locations:
Cards For Sale: ~35,000
Exposed Canada Locations:
Estimated Window of Compromise: May 2017 - Present
Exposed Locations: 51
Top-5 Exposed Locations:
Cards For Sale: ~90,000
This recent breach once again emphasizes the importance of a transition to the more secure EMV POS terminals in retail operations. Although many large retailers managed to migrate entirely from older generation magstripe terminals to EMV in 2017, several nationwide chains still have not done so.
The theft of five million payment cards is undoubtedly among the most significant credit card heists in modern history, and will negatively affect a large number of consumers in North America. On the other hand, in recent years, US and Canadian banks have advanced their fraud detection capabilities tremendously, which will allow them to minimize the impact of the hack on their customers.
However, considering the popularity of Saks Fifth Avenue and Lord & Taylor stores with international travelers, whose banks might have less effective anti-fraud controls, we anticipate a significant surge in fraudulent in-person purchases in the coming months, which will explicitly affect foreign banks.
Those who shopped at the retail stores of both companies, should either promptly replace their payment cards or setup transaction alerts to monitor for suspicious activity. At this moment we believe that online shopping websites were not affected and online customers are not at risk.
If you believe that your organization was impacted by the breach, and you are in need of complimentary in-depth exposure analysis, including a list of all confirmed compromised locations, please reach out to us directly via our standard contact form.