
The Joker’s Stash marketplace, one of the largest and most notorious dark web marketplaces for buying stolen payment card data, has advertised its next major breach since December 2019. The shop’s administrator, “JokerStash,” announced that it would include US, European, and global cards purportedly including geolocation data listing the cardholder’s state, city, and ZIP Code. The latest advertisement claimed that the cards would go live on January 27, 2020 at 11:00 PM EST. The full collection would include 30 million US records across more than 40 states, as well as over one million non-US records from more than 100 different countries.

Joker’s Stash began uploading records as advertised on January 27. The breach was titled “BIGBADABOOM-III” and appeared in four different bases. The records included the state geolocation information, but not the city or ZIP Code as previously announced. The listed geolocation data for added records ranged across 40 states. However, much of this data appeared to be falsified, and only six states appeared to be genuinely affected.
Gemini has determined that the point of compromise for BIGBADABOOM-III is Wawa, an East Coast-based convenience store and gas station. CEO Chris Gheysens claimed that the company discovered the breach on December 10, 2019, and removed the malware within two days. However, it had potentially infected all of Wawa’s payment processing servers and collected customer payment card data since March 4, 2019. This data reportedly included card numbers, expiration dates, and cardholder names. While the full extent of the breach remains unknown, it may affect all payment terminals and fuel dispensers at every Wawa location.
Since the breach may have affected over 850 stores and potentially exposed 30 million sets of payment records, it ranks among the largest payment card breaches of 2019, and of all time. It is comparable to Home Depot’s 2014 breach exposing 50 million customers’ data or to Target’s 2013 breach exposing 40 million sets of payment card data. Joker’s Stash has uploaded records from several major breaches in the past; Gemini determined that the previous edition by this naming convention, “BIGBADABOOM-II,” affected Lord & Taylor and Saks Fifth Avenue.
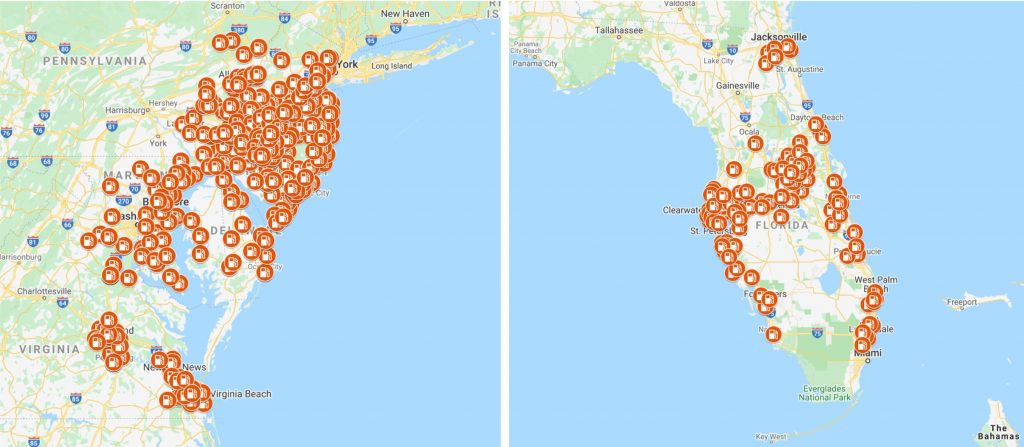

The Wawa breach aligns with Joker’s Stash’s tactic of adding records stolen from large merchants in publicly disclosed major breaches only after the breach is announced. Based on Gemini’s analysis, the initial set of bases linked to “BIGBADABOOM-III” consisted of nearly 100,000 records. While the majority of those records were from US banks and were linked to US-based cardholders, some records also linked to cardholders from Latin America, Europe, and several Asian countries. Non-US-based cardholders likely fell victim to this breach when traveling to the United States and transacting with Wawa gas stations during the period of exposure.
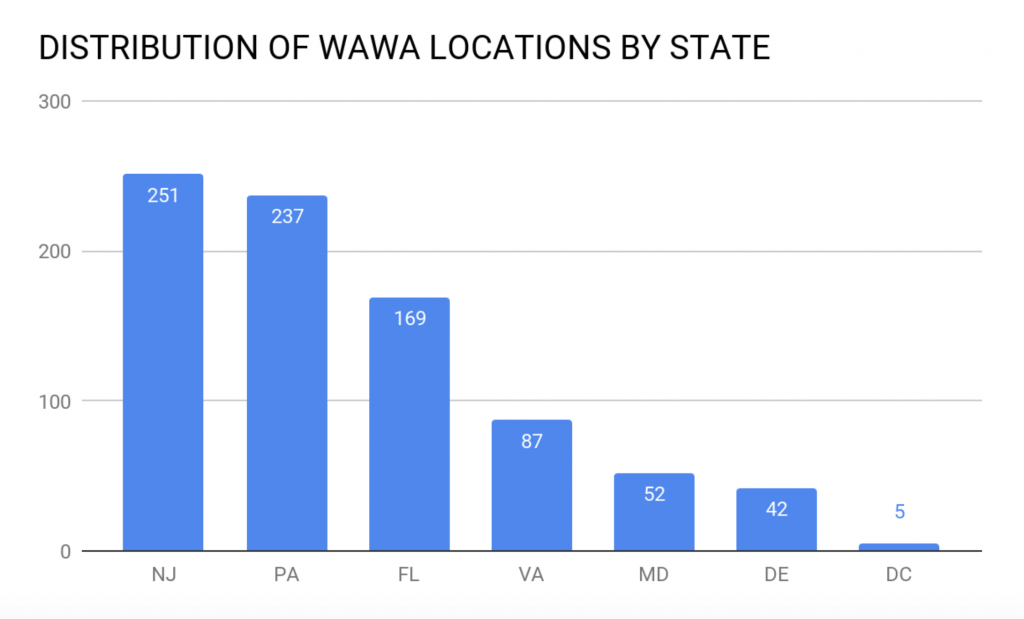

While Wawa has the most locations in New Jersey and Pennsylvania, according to Gemini’s analysis, the highest exposure of cards currently comes from Wawa locations in Florida, followed by Pennsylvania. As of this writing, analysts have identified compromised locations in all six states in which Wawa operates.
The median price of US-issued records from this breach is currently $17, with some of the international records priced as high as $210 per card. Apart from banks with a nationwide presence, only financial institutions along the East Coast have significant exposure. Notably, major breaches of this type often have low demand in the dark web. This may be due to the breached merchant’s public statement or to security researchers’ quick identification of the point of compromise. However, JokerStash uses the media coverage of major breaches such as these to bolster the credibility of their shop and their position as the most notorious vendor of compromised payment cards.
Gemini Advisory provides actionable fraud intelligence to the largest financial organizations in an effort to mitigate ever-growing cyber risks. Our proprietary software utilizes asymmetrical solutions in order to help identify and isolate assets targeted by fraudsters and online criminals in real-time.